7 Proxy Piercing Techniques: What Works in 2023?
Introduction With the rise of online tracking, proxy and VPN services have become a popular way to protect people's privacy. However, these digital shields also provide an opportunity for bad act...
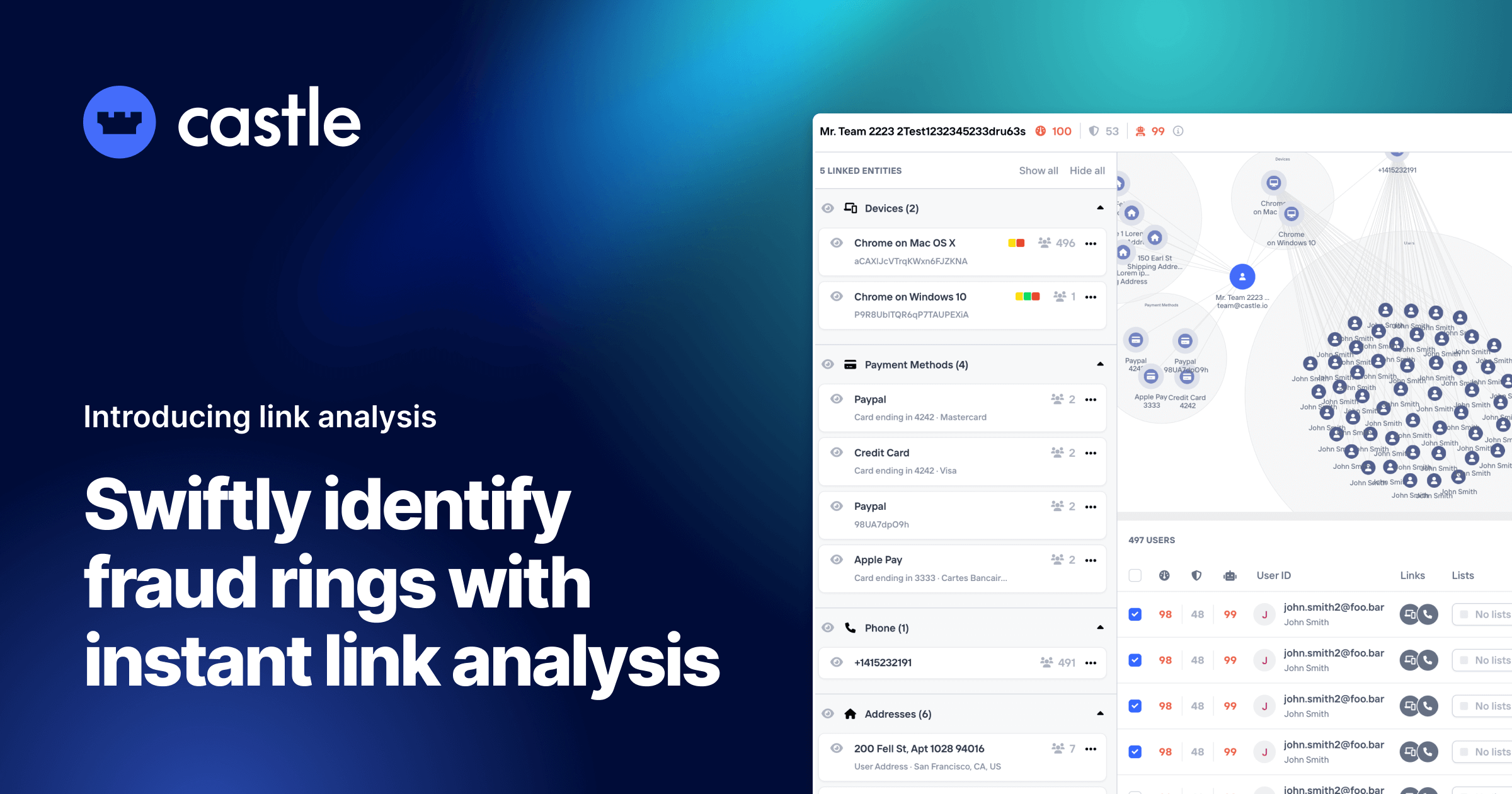
Swiftly identify fraud rings with instant link analysis
Castle is a real-time rules engine designed to manage fraud and risk across all touchpoints, including onboarding, login, payment, and content sharing experiences. We're excited to announce a new...
Enhanced User Activity Monitoring
When risk, product, and customer teams work together to prevent unwanted users from using their service, they usually lack the necessary information needed to make a quick determination between good o...
CyberNews Interview: Online businesses that handle money will be a target
Feeling like doing some quick online shopping through an attractive ad or signing up for a lucrative deal with a bank? Be wary: cybercriminals are lurking to exploit your personal information by setti...
A behavioral approach to device fingerprinting
Background Online businesses connect with their customers over the internet through a device, like a laptop or phone, using a web browser or an app. Having insights into these devices can help a busin...
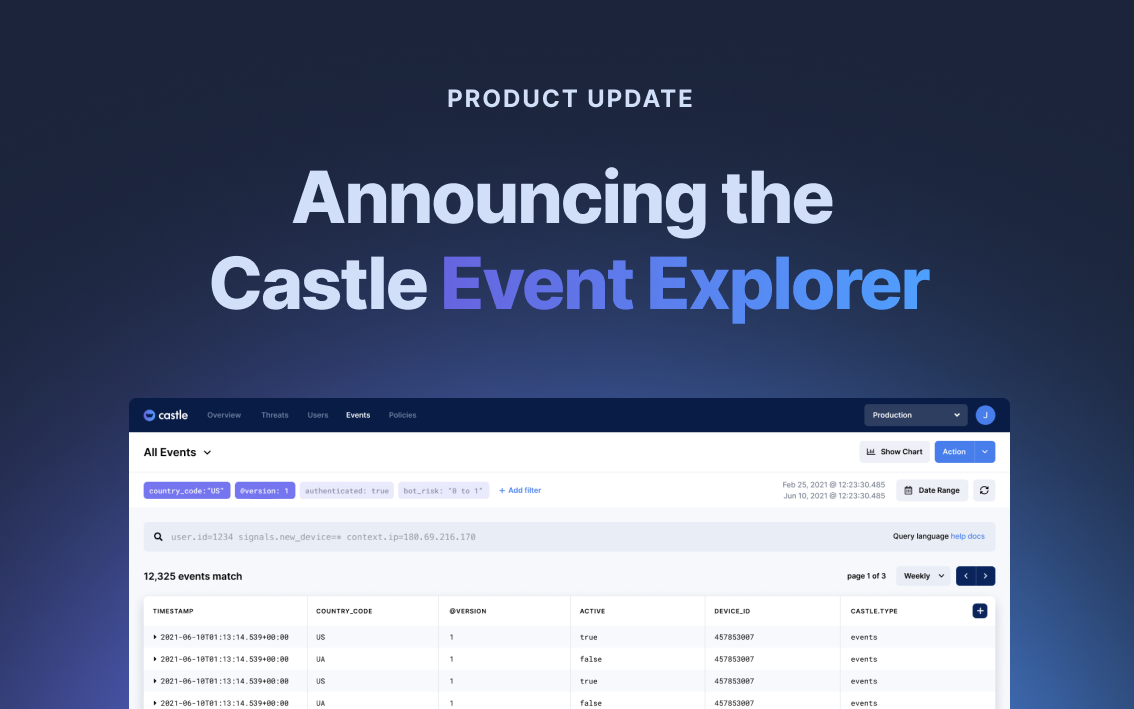
Announcing the Event Explorer
Today, Castle is releasing the Event Explorer, giving security and fraud teams a new way to discover and investigate malicious activity....