Introduction
With the rise of online tracking, proxy and VPN services have become a popular way to protect people's privacy. However, these digital shields also provide an opportunity for bad actors to hide their suspicious activity. This is where "proxy piercing" comes in. It's a set of techniques used to pierce these shields and reveal the true IP addresses of users, allowing the identification of bad actors.
What are the different methods used to uncover users' true identities and evaluate their effectiveness? What are the potential ethical and privacy implications of these methods? And how have modern browsers and privacy tools adapted to protect against IP leaks?
While proxy piercing techniques are valuable for identifying fraudulent activity, it is critical to remain aware of the potential risks and ensure that individuals' privacy is protected. As we enter an increasingly complex era of digital privacy and security, it is essential to understand the methods and tools used in this game of cat and mouse.
7 proxy piercing techniques
1. WebRTC leaks
With WebRTC, modern web applications enable video and voice calls, file sharing, and real-time chat. Supported by default in popular browsers such as Chrome, Firefox, and Safari, it significantly enhances the online experience. However, it's crucial to consider its potential privacy implications.
WebRTC is one of the more likely proxy piercing techniques to work, as leaks can occur in specific configurations, exposing a user's true IP address. Nonetheless, browser vendors have acknowledged these privacy concerns and made considerable efforts to mitigate WebRTC-related exploits. Users can further safeguard themselves by disabling WebRTC entirely or using browser extensions designed to block these leaks.
For a malicious actor's actual public IP address to be exposed, they would need to use a proxy or VPN without proper WebRTC leak protection. While this is a possibility, you should expect them to be using one of the many VPN services that now incorporate built-in WebRTC leak protection.
Here's a snippet of JavaScript you can paste into your developer console to reveal what WebRTC reports as your public IP. Let's hope it's the same as your proxy!
const pc = new RTCPeerConnection({iceServers: [{urls: 'stun:stun.l.google.com:19302'}]});
pc.createDataChannel('');
pc.onicecandidate = (e) => {
if (e.candidate && e.candidate.type === 'srflx') {
console.log('Public IP:', e.candidate.address);
}
};
pc.setLocalDescription(await pc.createOffer());You can also visit BrowserLeaks for a more comprehensive check for IP leakage.
2. Session monitoring
Session monitoring is a non-intrusive approach to proxy piercing, since it does not reveal a user's IP address nor exploit vulnerabilities. The use of device fingerprinting techniques, coupled with closely tracking each page view and interaction, can correlate anonymous traffic and identify the IP address a malicious actor used before logging in to an account. Using this method effectively would need the bad actor to make mistakes or be unaware of what is being monitored, but this is not uncommon.
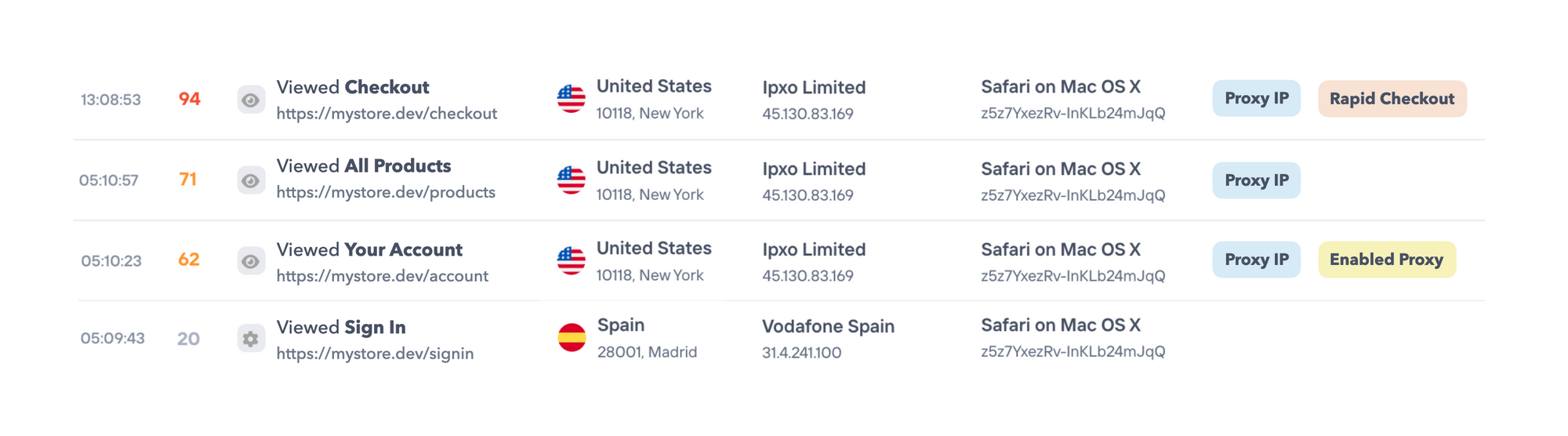
One of the key advantages of session monitoring is that it respects user privacy, as it operates on the premise that IP addresses are public information. Session monitoring strikes a balance between fraud prevention and preserving user privacy and trust by observing and analyzing user behavior rather than exploiting loopholes. This method demonstrates that it's possible to enhance security without compromising the privacy of individuals.
The following code snippet demonstrates a simple localStorage-based solution to monitor IP addresses on the same device using the ipstack API. It is important to note that this example does not utilize device fingerprinting, and as a result, it may not be suitable for production use. A more robust server-side solution such as Castle or Sift is recommended for accurately monitoring IP addresses across each page view in real-world applications.
And finally, the last activity type is “custom”, which can be used to track other activities, like adding an item to a shopping cart.
const apiKey = 'your_api_key';
const response = await fetch(`https://api.ipstack.com/check?access_key=${apiKey}&security=1`);
const data = await response.json();
const ipAddress = data.ip;
const isProxy = data.security.is_proxy;
const keyName = isProxy ? 'proxyIP' : 'trueIP';
localStorage.setItem(keyName, ipAddress);3. Adobe Flash
In the 2010s, Adobe Flash was a widely utilized technology for interactive web content, animations, and multimedia applications, even powering the popular online game "FarmVille." It was probably one of the most effective ways of revealing a user's true IP address behind a proxy, as it could access local network information without the user's knowledge.
As concerns about user privacy and security grew, major web browsers began to remove support for Flash. Adobe officially ceased support at the end of 2020, reflecting the industry's shift towards prioritizing user privacy. To think that the same technology that brought us countless hours of farming virtual crops also had a hidden power to harvest our true IP addresses.
4. Java Applets
Java Applets, like Adobe Flash, held a significant position in the web development landscape during the 2010s, with support from most major browsers. They powered various browser-based tools and plugins, such as the once-ubiquitous Java plugin for viewing 3D images in web pages. These applets enabled developers to leverage native Java networking libraries to bypass proxy settings and make direct connections to remote servers, making them attractive for fraud prevention vendors.
However, as security concerns mounted, web browsers implemented more stringent security measures, effectively reducing the efficacy of Java Applet-based proxy piercing techniques and leading to their decline in modern web development.
5. ActiveX Controls
ActiveX controls, primarily supported in Internet Explorer, offered another avenue for bypassing proxy settings and revealing a user's true IP address. These controls powered interactive web features, like the famous "Marquee" control for scrolling text and images, which was a popular design element during the early days of the internet. However, the same playful widget could also slyly fetch a user's real IP address behind the scenes, exposing their privacy.
As security concerns grew, Internet Explorer implemented stricter measures, causing fraud detection solutions to abandon ActiveX controls to avoid inadvertently prompting users for access. Microsoft Edge, the successor to Internet Explorer, forgoes native ActiveX support in favor of modern web technologies and a more secure extension model, ensuring a safer browsing experience for users.
6. DNS leaks
DNS leaks are not considered an effective method for revealing a user's true IP address when the user is behind a properly configured proxy or VPN. In cases where a user's DNS queries might bypass the proxy or VPN, it is possible that their true IP address could be revealed. However, many VPNs now provide built-in DNS leak protection, and users can take additional precautions by using a custom DNS server or configuring their device to prevent DNS leaks.
There are several factors that can contribute to DNS leaks, but they are often due to misconfigurations or application-specific issues:
Application-specific proxy settings: Some applications have their own proxy settings independent of the system-wide proxy settings. If an application's proxy settings are not configured correctly, it might send DNS queries directly, bypassing the proxy, while still using the proxy for HTTP requests.
Partial proxy configuration: Proxy settings can be applied to different protocols (e.g., HTTP, HTTPS, SOCKS, etc.). If the proxy configuration is applied only to the HTTP protocol and not to DNS, it could result in DNS queries bypassing the proxy and revealing the true client IP.
7. HTTP headers
HTTP headers can also be examined for information about the client's IP address. Some common headers that might contain IP information include X-Forwarded-For, X-Real-IP, X-Client-IP, X-Cluster-Client-IP, and Forwarded. However, this method requires a broken VPN service or incorrect proxy configuration and is therefore unlikely to be successful in revealing a user's true IP address.
For example, if the proxy server is configured to add the client's IP address to the header, but fails to remove any existing IP addresses in the header, the client's real IP address may be included in the header alongside the IP address of the proxy server. This could happen if the proxy server software is configured with incorrect or incomplete rules for modifying the header or if there is a bug in the software.
So what works in 2023?
As we navigate the ever-evolving landscape of proxy piercing techniques, striking the right balance between robust fraud detection and user privacy preservation is crucial.
Our summary of what's possible in 2023, ranked by reliability and privacy:
| Technique | Reliability | Privacy | Limitations |
|---|---|---|---|
| Session Monitoring | High | Yes | Requires the user to make mistakes and be unaware of monitoring |
| WebRTC Leaks | Medium | No | Relies on user errors or misconfigurations |
| HTTP Headers | Low | No | Requires broken VPN service or incorrect proxy configuration |
| DNS Leaks | Low | No | Relies on user misconfigurations |
| Adobe Flash | Obsolete | No | Major browsers ended support in 2020 |
| Java Applets | Obsolete | No | Dropped by Chrome in 2015, and Firefox in 2017. Deprecated in 2018 |
| ActiveX Controls | Obsolete | No | Microsoft Edge released in 2015, which doesn't support ActiveX |
WebRTC leaks and session monitoring emerge as the most viable options in this cat-and-mouse game. Session monitoring, in particular, demonstrates that it's possible to strike a balance between robust fraud detection and preserving user privacy by focusing on user behavior analysis.
However, gaining visibility into your users' journey is only as effective as the tools and methods employed. Proxy piercing techniques, while powerful, require the right insights and management to make a difference.
Fraud detection should employ a comprehensive understanding of user behavior, combined with the ability to effectively analyze and interpret this data.
Castle is designed to help you harness the power of these components in the realm of proxy piercing techniques. By providing fraud managers with enhanced visibility into the user's journey, Castle serves as the first step towards a safer internet experience for both businesses and users.


