
How to Think About GDPR as a Security Vendor
Learn about essential aspects of GDPR, and how security vendors like Castle can provide tools that actually make it easier for app developers to adhere to fundamental GDPR regulations....


Learn about essential aspects of GDPR, and how security vendors like Castle can provide tools that actually make it easier for app developers to adhere to fundamental GDPR regulations....
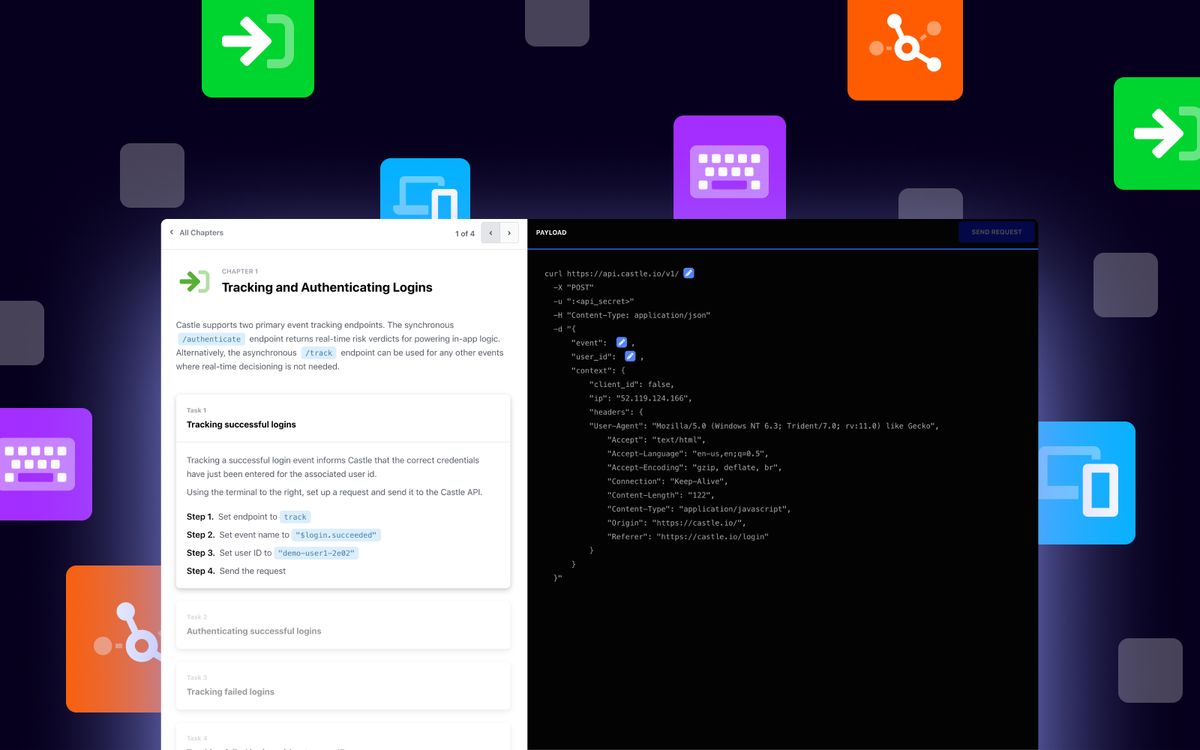
The Training Camp runs developers through the Castle basics: Get hands-on experience with Castle's APIs, a deeper understanding of Castle features and more!...

Get a solid understanding of the differences between attacks and anomalies that will allow you to create workflows that put the user first....

We are excited to share a new feature in the dashboard that is aimed to help make the Castle Integration more friendly and self service for developers!...

At Castle, we are focused on building tools that power end-to-end user security alongside a frictionless user experience....

One item that is commonplace in a hacker’s toolset is a database of leaked user credentials. The database holds a set of exposed user login credentials......