At Castle, we are focused on building tools that power end-to-end user security alongside a frictionless user experience. We believe that when it comes to protecting your users, the ability to detect unauthorized access to their accounts is just the beginning. Beyond the detection, developers are using Castle’s APIs to block the unauthorized access in-line, notify their users in real-time of account breaches, and automate the account recovery process.
For example, if a malicious entity tries logging into your user’s account with their actual credentials, the first step is to recognize it. Once detected, you can block it’s attempt. But the story does not end here. Detecting and blocking are critical first steps, but your user’s credentials are still in a compromised state — that bad actor still has their active username and password. Until your user resets their password, their account remains at risk as the bad actor can make return attempts with the same set of stolen/leaked credentials, slightly altering their behavior until they are able to avoid detection.
For this reason, Castle helps our customers automate end-to-end user security, from detection through account recovery, including:
- Detecting suspicious and malicious entities on user accounts
- Blocking bad actors from accessing user accounts
- Notifying users when their account is compromised or at risk
- Tracking password resets to confirm accounts are recovered and cases are closed

With the proper tools, applications that want to look out for their users can automate the swift movement of compromised users through this entire Account Recovery Funnel. By looking at the bigger picture and implementing end-to-end user protection and account recovery in this way, developers are not only keeping the bad guys out, but also keeping their users safe.
You have to see it to believe it
Delivering great security tools is the end goal. However, blindly trusting any blackbox tool is a risk for any developer. Without digging into logs and outbound email systems, we want to make it easy for developers to answer that fundamental question: “Am I keeping my users safe?”. Keeping the Account Recovery Funnel in mind, we’ve launched a series of initiatives to build up the analytics, insights, and tools offered around this question.
First up is a set of new graphs on our Dashboard’s Overview page aimed at highlighting key trends and day to day insights around each step in the Account Recovery Funnel. The new Overview page in the Castle Dashboard includes 4 new charts that highlight what your Castle integration is seeing and doing. Below, we’ll break down each of the graphs to explain what they are showing and what insights can be gained from them.
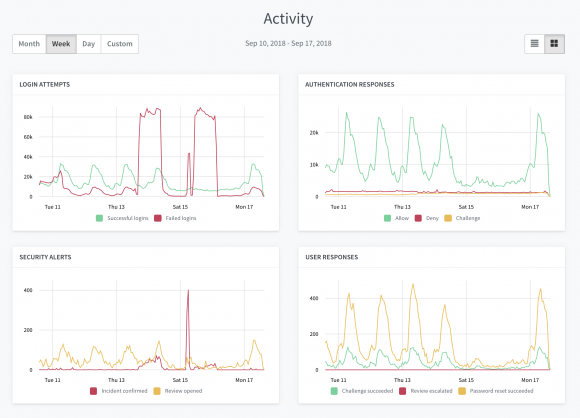
Logins Succeeded vs Logins Failed
Castle Integration Pre-requisites: Objective 1: Protecting Your Login
One of the most obvious indicators of a large-scale attack targeting your users is a spike in login attempts. Attackers armed with a database of leaked emails and passwords often jump from site to site, running through the database with automated login attempts to see if any are any valid matches. When this happens, a spike in login attempts becomes apparent. This simple, yet powerful graph, helps you detect times when your site comes under attack.
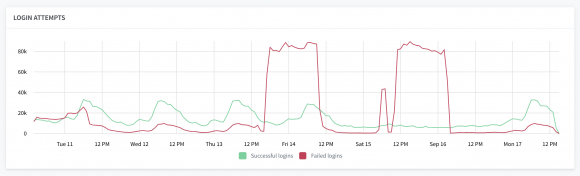
Adaptive Authentication Responses
Castle Integration Pre-requisites: Objective 1: Protecting Your Login
Castle’s adaptive authentication is the last line of defense to ensure that bad actors are not able to access your user’s account, even if they got hold of your user’s login credentials. Whenever you use Castle’s API to authenticate a key event on a user’s account (i.e. a login, profile update, or transaction), Castle will determine if the entity attempting the event is in fact the account owner and return a synchronous verdict inline. One of three possible verdicts instruct you how to safely handle handle the event:
- Allow — This is the true account owner, you can confidently commit this event.
- Deny — This is an abusive actor, block this event from being committed.
- Challenge — This behavior is out of the norm for this user. Additional verification should be requested before committing this event (i.e. 2FA).
This graph will show you the total volume of each verdict that is returned over time. Whenever there is a suspicious spike in Successful Logins on the first graph, it would be common to also see an aligning spike in Deny and Challenge response on this graphs. This will show you how Castle is helping you to respond and block bad actors in real-time, even when they got hold your user’s credentials.
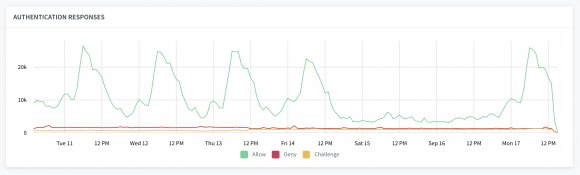
Security Alerts
Castle Integration Pre-requisites: Objective 1: Protecting Your Login, Objective 2: Account Recovery, Objective 3: Engaging Your Users
Whenever a device is challenged or denied via Castle’s Authentication API, it is a signal that a malicious entity has knowledge of a user’s credentials. Even though their action was blocked in real-time, the user is still at risk as long as they are relying on a compromised set of credentials. As such, it’s important to alert the user right away so that they can review the activity, and in the case of a confirmed compromise, they can take the steps needed to reset their password and secure their account.
As soon as Castle notices unusual activity on an account, we send a server-to-server webhook notifying our customers of the event, the user at risk, and the details around the activity in question via a JSON payload. Developers use our webhooks to power automated security alerts and notifications to the end users (i.e. emails or push notifications), directing users to review suspicious activity on their account, or in the worst of cases, to reset their password.
Castle offers two flavors of webhooks:
- Review Opened — Sent once per device, when an anomalous device or unusual behavior is detected on a users account. The user should review the activity and provide feedback to approve or report it.
- Incident Confirmed — Sent once per device, when a known abusive device has been detected trying to access a users account. The user should reset their password immediately in order to recover their account.
This graph will show you the total volume of each webhook sent out over time. Whenever there is a spike in the above graph, it would be common to also see an aligning spike in webhooks sent out. This will show you how Castle is powering your automated security notifications to users that kickoff the account recovery workflow.
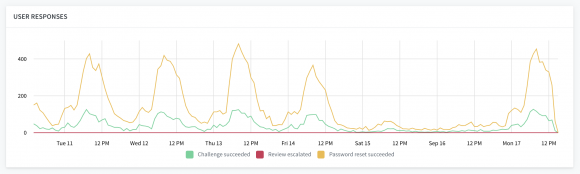
User Feedback
Castle Integration Pre-requisites: Objective 1: Protecting Your Login, Objective 2: Account Recovery, Objective 3: Engaging Your Users
The Security Alerts graph above shows how users are being notified of suspicious and compromising events on their account. These alerts encourage users to review the activity in question, or reset their password if their credentials were compromised. In both cases, developers can feed the action that the user takes back into Castle to update their users risk models. Tracking user feedback is a key step to completing the Account Recovery Funnel and closing cases of suspected or confirmed account takeovers.
For this reason, in the aftermath of an attack, it’s important to know if impacted users are taking action in response to their security alerts. This User Feedback graph tracks the different types of user feedback:
- Challenge Succeeded —A user has successfully completed an inline challenge, or they have reviewed suspicious activity on their account and approved it. The user’s account is in a safe state. This activity will become part of the users behavioral norms.
- Review Escalated — A user has reviewed suspicious activity on their account and reported it as unauthorized use. This will be escalate into a confirmed incident. The user’s account is in a compromised state.
- Password Reset Succeeded — A user has reset their password. If their account had been compromised, the incident has now been mitigated. The user’s account is in a safe, recovered state.
Whenever there is a spike in the above graph, it would be common to also see an aligning rise in the User Feedback graph in the hours and days following (there is typically a delay as users may not read or react to security alerts in real time).
Seeing It Through
It’s always important to educate your end users of security best practices — using secure passwords, never reusing passwords, using 2FA whenever it’s available — but in reality, only a small percentage follow good security hygiene.
We are hearing from more and more developers recently who are seeing this first hand, and are therefore taking on a new sense of responsibility when it comes to protecting their users’ accounts. Many are eager to receive alerts whenever an individual account is compromised. They want to automate security notifications to that account owner, and they want to ensure the account gets fully recovered. They want to see it all the way through. And with the growing trend of major user-focused policies like GDPR and California’s Security Breach Notification laws being introduced, they don’t want to wait for this approach to become a requirement. It’s encouraging to see this responsible innovation taking place around higher standards and deeper levels of insights ahead of the curve.
We believe in this mindset and approach as well and want to support it. Castle’s products are designed for the developers and teams of all sizes taking on this new responsibility. In their effort to see users all the way through the Account Recovery Funnel, these graphs — along with additional features on the way 😉— are helping teams get the clarity and traction needed to stay ahead of the account security curve.






