One item that is commonplace in a hacker’s toolset is a database of leaked user credentials. The database holds a set of exposed user login credentials — user emails and corresponding passwords for a given site or application. What makes a list like this so valuable for hackers is the fact that most people reuse their passwords across multiple applications. So if a hacker gets hold of a leaked set of credentials from just a single site, it can actually be tried as a skeleton key, breaking them into user accounts across a limitless range of sites.
Leaked credentials often show up first on the dark web as valuable loot one has extracted during a successful breach of an application’s database. Over time, the leak will circulate. Recently, published leaks have become more common on public sites and forums across the web. Some are modest in size, holding a couple hundred login credentials. Others are shocking in scale, such as one in December that boasted 1.4 billion clear text credentials that were even organized into an interactive, searchable format.
With credential leaks becoming larger, more common, and more public, it has lead to a surge in attacks at the login endpoint and account takeovers. Some attacks have malicious intent, others are just hacker hobbyists toying around with a new bot. Regardless of the intent, each leak provides hackers with a shiny supply of fresh ammunition to crack into unsuspecting user accounts.
White hats are aggregating databases too
Thankfully, there are some good samaritans looking out for the people. Troy Hunt, for example, created “Have I Been Pwned?” (HIBP), which is an app that maintains an ever-growing aggregate of leaked email addresses. This database is used as a way to inform users whenever their email turns up in a new leak. Anyone can use the tool to perform an ad-hoc lookup of their email address and learn if they have been compromised in any known leaks. You can also subscribe to receive instant alerts in the event that your email turns up in a fresh leak. This amazing tool allows people to stay informed and take swift action to reset their passwords before any of their accounts become compromised due to a published leak. On top of this, HIPB has partnered with 1Password, a tool that makes it super simple to create and track unique, secure passwords for each site you log into. The combination of using unique passwords per site while also being informed whenever your credentials may have been involved in a breach is a huge win for user security and preventing account takeovers.
Unfortunately, web security is not top of mind in most peoples daily lives. Very few utilize these incredible tools at our disposal. According to Hunt, of the 3.1 billion unique leaked emails are tracked on HIBP, only 2 million — a mere 0.06% — have subscribed to the notification service. The truth is, most of us aren’t proactive in security, making us sitting ducks to an account takeover attack if our credentials show up in a leak.
Looking out for the users
What if there were an extra set eyes looking out for us? What if there were some “guardians” in our digital lives that had our backs, that monitored our exposure and notified us of risks? What if the sites and applications we love and use every day felt a shared sense of responsibility for their users — could they play this role? This would require a certain type of site, one that truly places high value on their users and cares about safety and security. Enough so that they would take extra steps to look out for us. These are exactly the types of sites Castle works with. So here at Castle, we’re building new tools to help our customers shine in this “guardian” role.
Similar to HIBP, Castle is also maintaining an aggregated database of leaked credentials. At over 1 billion entries and growing, we are now integrating this database into our core product offerings.
Our objective is to help our customers look out for their users and prevent account takeover. The first step to doing so is surfacing which of their users have been found in credential leaks. We are making it easy for our customers to quickly identify which users are at higher risk of targeted attacks due to credential leaks. With this information easily accessible, sites and applications that utilize Castle are in a better position to protect and look out for their users.
View it in action
At Castle, we have already been utilizing our leaked credentials database behind the scenes for some time. For example, it functions as a weighted input into our user risk models. With recent updates to the Castle UI, we are now excited to be able to share key insights with our customers via the Castle Dashboard. There are a few areas where insights from the leaked credentials database is already integrated, with more features on the way.
Note to Castle Customers: If you are already passing emails within the user_traits object via track and/or authenticate calls, the following insights will automatically populate in your dashboard. No changes to your integration are needed.
User View
When viewing a single user, if that user’s email had been found in any breach, you notice an icon next to their email along with the amount of breaches this user had been found in. Note: For user protection purposes, we do not openly expose which breaches they were a part of.
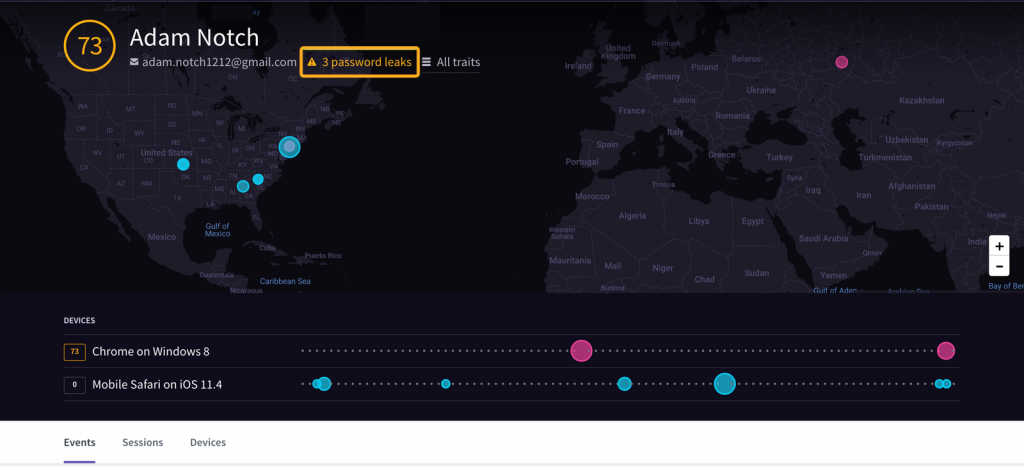
User Search View
When searching through your users, you can now filter them by users that were found in credential leaks. By clicking “Part of password leak”, we will show only users who have an email that has been found in our database of leaked credentials.
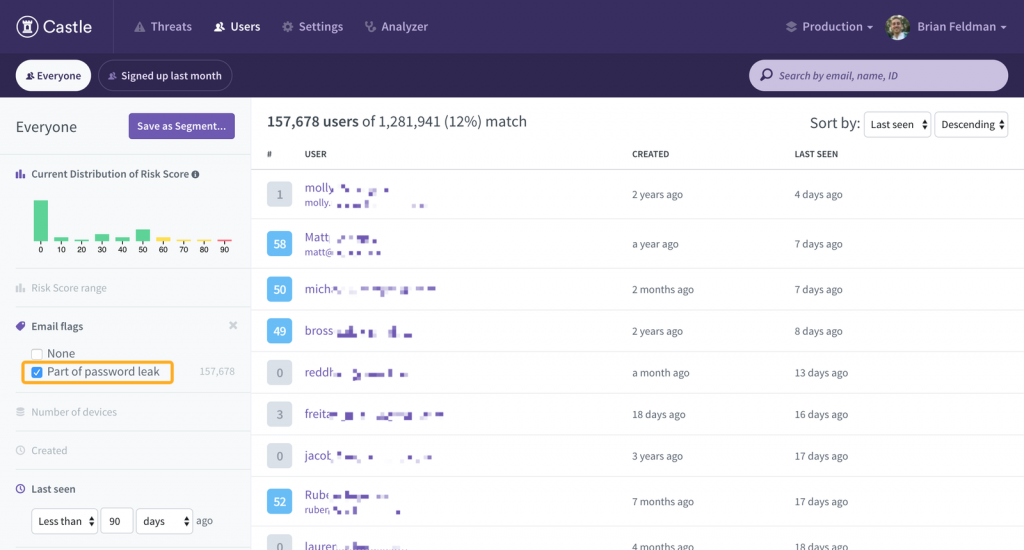
Much more to come!
This is just the start. We have more items on the way, including graphical overlays, subscriptions/notifications of new leaks is discovered, and more.






