For an early stage company, the focus often lies in attracting users and expanding the customer base. Land and expand. During this phase, account sharing may not be perceived as a significant problem. However, as the business matures and revenue optimization becomes the primary focus, the detection and management of shared accounts become crucial and can be a relatively low hanging fruit effort to uncover more revenue.
Subscription businesses, especially those with pricing models based on the number of seats, encounter distinctive hurdles. Netflix, known for its previous tolerance towards account sharing, recently underwent a notable transformation by tightening its stance on password sharing in the United States. This serves as a significant reminder of the importance of addressing this matter in an oversaturated streaming market.
The Phantom Menace
Recent reports indicate that the practice of password sharing has resulted in significant revenue losses for Netflix, with over 100 million subscribers worldwide engaging in this activity. This revelation was further supported by Netflix's first decline in subscribers in over a decade in April 2022. Despite the addition of 7.66 million new subscribers in the final quarter of 2022 and a net increase of 1.75 million subscribers in the first quarter of 2023, the impact of account sharing on revenue remains undeniable. This reality emphasizes the urgent need for businesses to devise robust strategies to combat account sharing and maximize their revenue potential.
The Principle of Do No Harm
To detect account sharing, it is vital to understand how to identify such instances, and how to do it with high precision in order to not upset legitimate users. Key functionalities like device fingerprinting and advanced rules engines equipped with real-time velocity queries play a crucial role in this process.
One established approach involves analyzing the number of unique IP addresses and device fingerprints associated with an account within a specific period. Flagging accounts that display outlier behavior, such as a significantly higher number of IPs compared to the average, indicates potential account sharing. It is important to consider legitimate scenarios, such as multiple users from the same IP address due to family or company usage. For more precise results, counting device fingerprints can provide a reliable indicator of multiple users. Additionally, implementing limits on the number of allowed device types can act as a deterrent to account sharing.
Return of the Jedi
Although these detection methods are somewhat effective, resourceful users have found ways to circumvent them. Techniques like using VPNs or connecting via the account owner's Wi-Fi are employed to bypass conventional restrictions. These tactics underscore the need for a more comprehensive and sophisticated approach to tackle the ever-evolving challenges posed by account sharing.
The Force Awakens
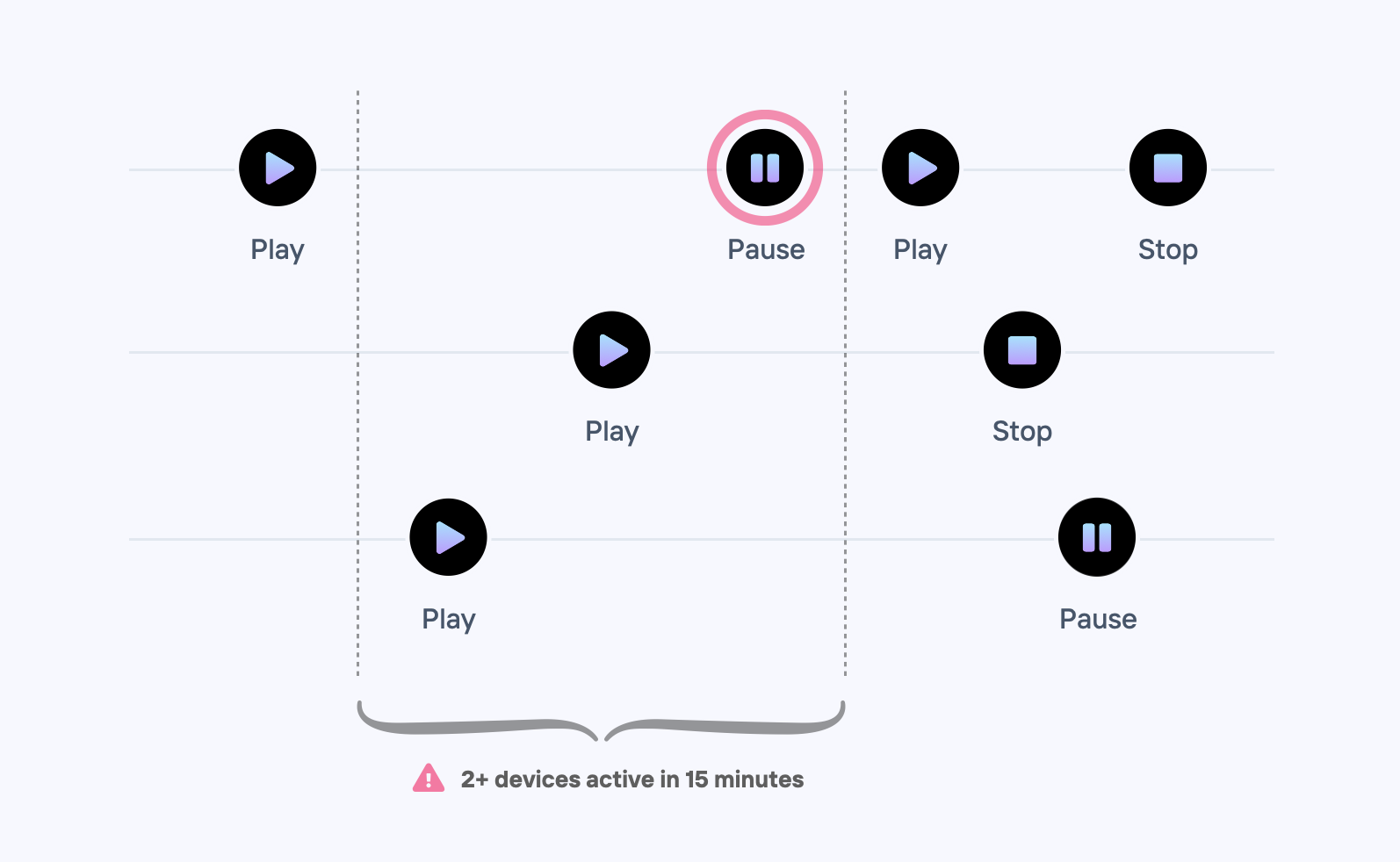
To tackle the complex challenges of account sharing, businesses need a solution that goes beyond traditional methods. The real solution lies in continuously tracking user events, providing more fidelity in detecting overlapping activity. Companies like Netflix, for example, may track events such as "Stream started," "Stream playing," and "Stream stopped" to gain insights into user behavior and estimate instances of overlapping usage by aggregating usage using sliding window functions. By monitoring high-frequency events, businesses can achieve more accurate results in identifying account sharing. If you don't know exactly what events to track, a simple approach is to track page views or mobile screen views.
While these tools have their merits in addressing specific forms of abuse, such as automated attacks, they often fall short in combating the wide range of account abuse, including account sharing that is typically performed by humans.
By continuously monitoring user navigation and critical events within a customer's application, Castle gains unique insights into user behavior and patterns. This real-time monitoring enables the identification of irregular activities, such as overlapping usage indicative of account sharing. With Castle's comprehensive suite of features designed specifically to detect and prevent account sharing, businesses can effectively combat this challenge and intercept potential loss of revenue.
In addition to robust detection capabilities, it is crucial to prioritize the detection of account sharing by placing it at the forefront of the rules for blocking abusive behaviors. By giving the account sharing rule precedence, businesses can directly address this specific issue and allow subsequent account security rules to capture any remaining aberrations in user sessions. This approach ensures that account security efforts are not compromised and helps mitigate noise in the data.
With Castle's flexible solutions, tailored to each business's unique account sharing policies, companies can safeguard the integrity of their user base and maximize revenue potential. By adopting a continuous monitoring approach, businesses can effectively combat account sharing and ensure a secure and profitable environment for their users.






