At Castle, we believe in the power of APIs. APIs that help you protect your business from fraud and abuse. While some companies in our industry chose to obfuscate how their solutions work, we’re taking a different approach.
Today we’re pleased to announce our newest feature release, Risk Signals!
Risk signals have always been a part of Castle’s risk assessment engine, and with this release, that data is now returned on calls to the /authenticate API. This allows you to enrich your own data sets with a wealth of new information. Fraud and security teams in particular will benefit from this extra context, whether it’s sent to a logging system or forwarded to an analytics tool.
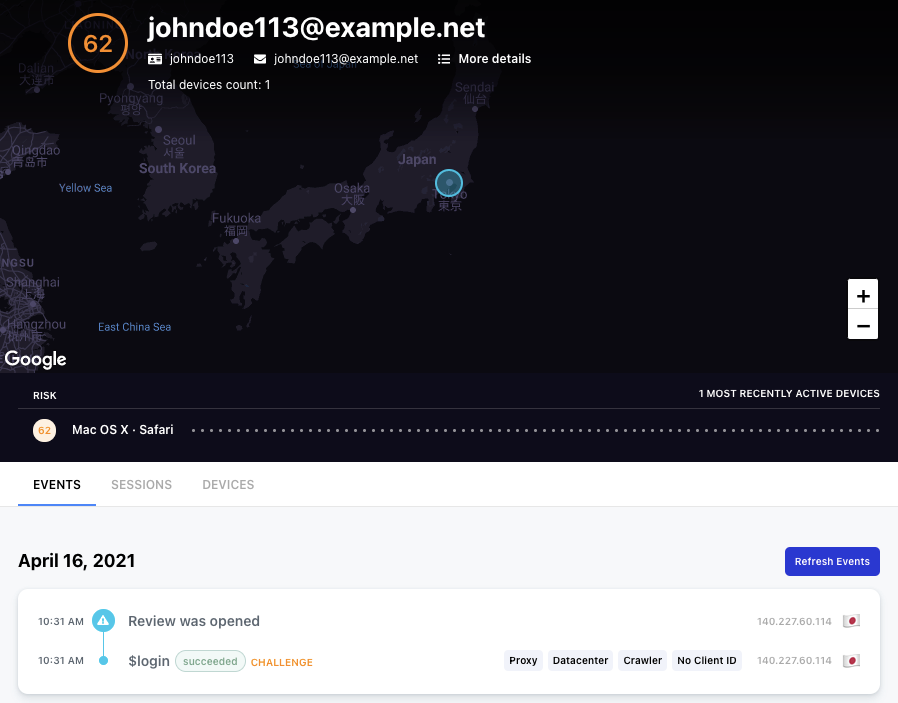
Castle’s risk signals are now exposed in both the Castle dashboard and in the /authenticate API, giving you visibility into data that was not accessible before.
From the dashboard, you’ll be able to better analyze attacks and suspicious activity. Risk signals triggered on an event provides helpful context that explains why a risk score is heightened.
Also, the /authenticate API now responds with the risk signals that triggered for that call. This gives developers access to a wealth of new information that can be used to enhance decision making. Inline logic can now be written to respond to certain signals, for example, block all headless browsers. Moreover, the risk signal data can now be logged for troubleshooting and analytics purposes.
In addition to exposing signals that were previously available in the Castle dashboard, some new signals have been introduced as well. With this release, new signals such as “high activity IP”, “spoofed device”, “bot behavior” and “headless browser” are now available, just to name a few.
{
"action": "challenge",
"user_id": "4xs8daf",
"device_token": "eyJhbGciOiJIUzI1gUaca0KQhwiao",
"risk": 0.93,
"signals": {
"bot_behavior": {},
"proxy_ip": {},
"disposable_email": {},
"spoofed_device": {},
"multiple_accounts_per_device": {}
}
}To see a full enumeration of our exposed Risk Signals, check out the documentation here.
Pro plan environments will see this functionality starting today, while users not on our Pro plan can reach out to have it enabled, free of charge. For those that need to request the upgrade, the upgrade process is simple and requires no more than an update to one line of code.
If you aren’t already using Castle and want to start protecting your end user accounts while enriching your dataset with risk data like this, you can sign up for a free trial account and get started here.







