In the fight against online fraud and abuse, we believe that the strategic advantage lies in flexibility and adaptability. Castle Policies is designed to be the backbone in implementing this strategy, and this is why we've been working on enhancing this experience lately.
Policies lets you create tailored rules that suit your specific needs. It’s designed to work in various scenarios, whether you're dealing with account abuse, account takeovers, or combating SMS-pumping. The key lies in the adaptability, and when used together with Custom Signals and Lists, it allows you to construct your unique defense line.
We've recently improved Policies based on user feedback and real-world application, and in this post I’ll highlight a few of them. Our goal was simple - make Policies even more effective and easier to use.
Re-designed UI
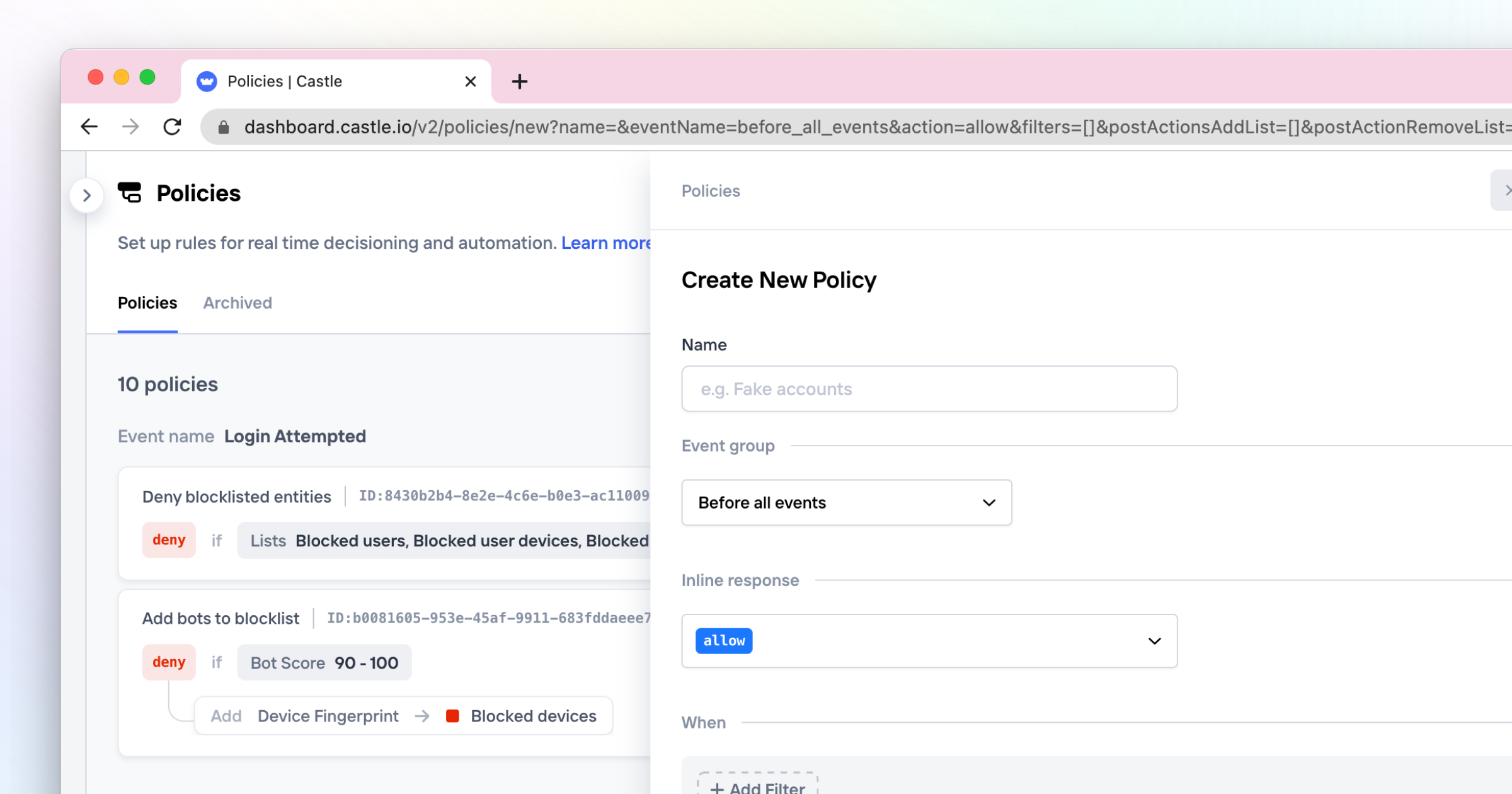
As the number of Policies grows, managing them can become a complex task. Our redesigned UI for the policy management page aims to give you a clearer, more readable overview of your system configuration. We've designed the UI to read almost like plain English, displaying the trigger condition, the inline action taken (allow, challenge, deny), and any configured side effects (e.g., Add/Remove from Lists). All this to instill confidence when making changes and to facilitate team discussions.
Since ideas for new policies often start with exploring data, we've also added a way for you to create a policy directly from the Explore view: when you've found an interesting pattern that you'd like to take action on simply click "create a policy" in the top right corner. This feature is an example of how we strive towards enabling you to quickly adapt to new attacks and types of fraud.
Policies without inline action
Castle Policies work like firewall rules, evaluated from top to bottom. Usually, when a policy matches, the configured inline response is returned in the Castle Risk/Filter APIs, halting the evaluation. But sometimes, you just want to monitor suspicious activity without taking inline action. Enter our new pass-through Policies.
These allow you to set up rules for flagging users without halting the evaluation process—perfect for monitoring suspicious activity like users sharing the same account. Paired with our newly launched Slack alerts, you can set up a lightweight alert flow for proactive detection and engagement.
More actions
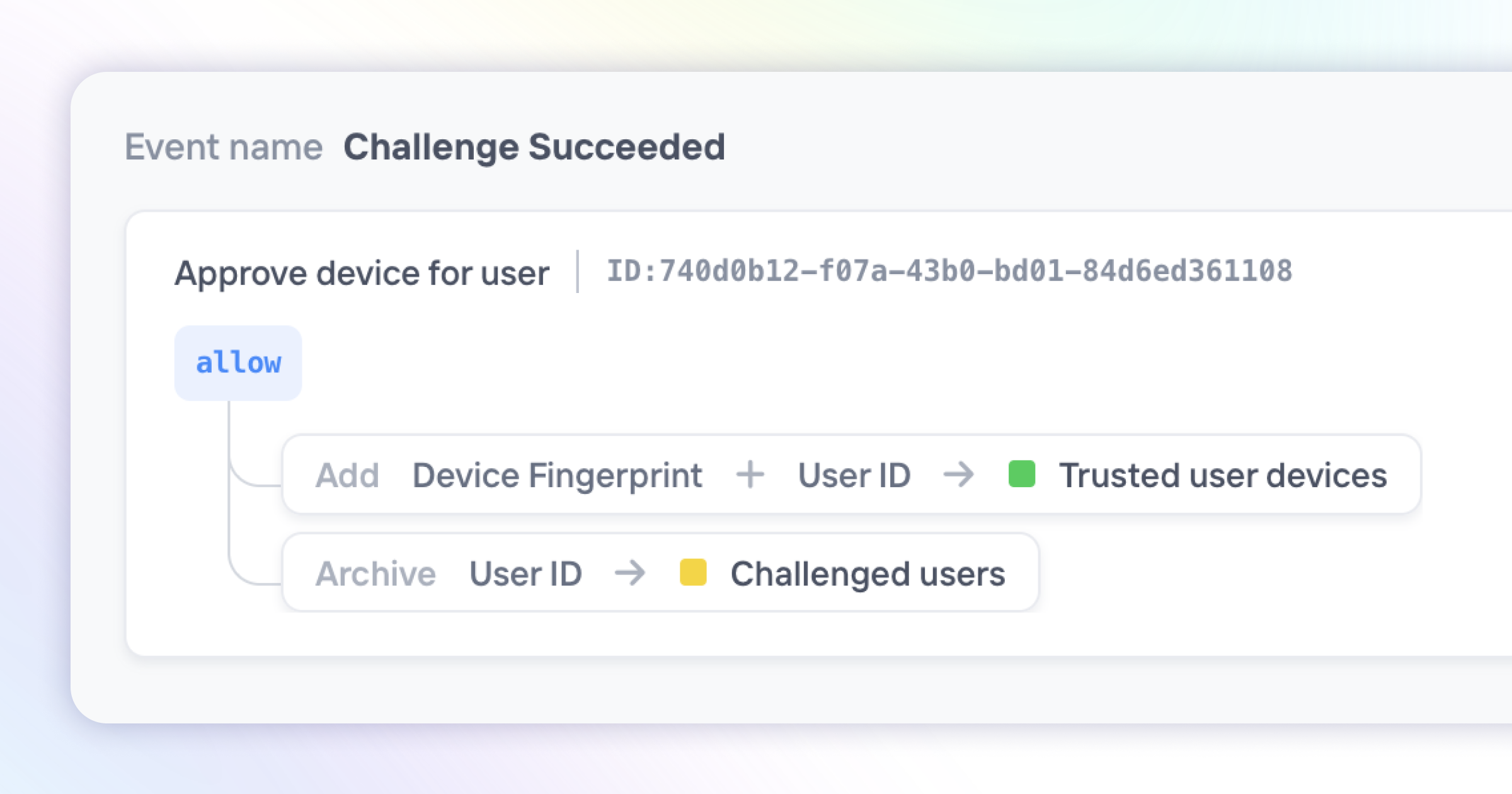
At its core, a Policy is a combination of a trigger condition and a set of corresponding actions. We've added more actions for you to choose from, the latest being the ability to remove items from Lists. This is particularly useful for actions like removing users from block lists after they've passed verification.
With Policies, the possibilities are endless. For example, many of our customers have created advanced step-up authentication systems where a device can be trusted for 30 days after successfully completing a challenge—like what you'd see at big tech companies.
Ultimately, with Policies, you're not merely reacting to fraud threats. You're proactively shaping your defense mechanism to ensure it remains as dynamic and adaptable as required in the digital landscape.
As always we're eager to hear your feedback on how we can improve Castle, just drop us a line at support@castle.io

