Disposable email addresses are temporary inboxes that allow users to receive messages without linking the address to a long-term identity. Unlike Gmail or Outlook, which are built for ongoing use and personal association, disposable email services are built for anonymity and convenience.
Most disposable services require no signup or verification. You simply choose a temporary address and can immediately receive emails. Messages are typically deleted after a few hours or days, making these services useful for avoiding spam or bypassing one-time email verification, but equally useful for abuse at scale.
Disposable emails generally fall into two main categories:
- Ephemeral inboxes: These are short-lived, single-use addresses with no persistence. They’re designed to expire after a short duration or after receiving a message.
- Email aliases: These act as persistent relays, forwarding messages to a user’s real inbox while masking their primary address. They offer better integration and longer-term utility, especially for privacy-focused users.
Why do people use disposable emails?
There are legitimate reasons for using disposable email addresses. Privacy-conscious users often want to protect their primary inbox from marketing emails and limit cross-site tracking. Disposable addresses allow people to sign up for services or download gated content without exposing their real identity or committing to ongoing communication. This isn’t just a niche behavior. Mainstream services like Apple’s Hide My Email now offer similar functionality, generating random addresses that forward to a user’s actual inbox.
At the same time, disposable emails are one of the most common tools used by attackers. Because these addresses are not tied to a real identity and can be created in bulk, they are ideal for mass-producing fake accounts. A single attacker using a bot can generate thousands of disposable email accounts in minutes. Once these accounts are live, they can be used for a variety of abuse scenarios:
- Free tier abuse: Attackers register repeatedly using disposable emails to exploit free trials or signup credits. This can lead to significant costs, especially for AI SaaS platforms with high compute usage.
- Spam and unsolicited content: On messaging or social platforms, fake accounts are often used to flood systems with spam.
- Ranking manipulation: Fake accounts can artificially inflate metrics like video views, streams, or likes, distorting content popularity.
- Payment fraud: Disposable emails are often used to test stolen cards or execute fraudulent transactions at scale.
- Phishing and scams: Attackers may impersonate real users or brands to steal credentials, distribute malware, or mislead others.
- Account takeover (ATO): In some cases, attackers take over real accounts using credential stuffing or breach data, then replace the associated email with a disposable one. This locks out the original user and allows the attacker to resell the account, particularly in gaming environments where in-game assets have real value.
How disposable emails affect online platforms
Disposable emails can cause a surprising amount of damage if left unchecked, even outside of obviously malicious use cases.
- They burn resources: Every fake account using a disposable email costs real infrastructure. You might be storing user data or sending emails, but the bigger hit comes when bots start triggering workloads tied to GPU usage, things like image generation, large language model inference, or speech processing. If attackers script thousands of signups and run free-tier prompts or jobs, it can rack up significant GPU hours fast. For platforms like ChatGPT, Claude, or any custom model hosted on a cloud GPU stack, the waste adds up quickly.
- They mess with your data: Disposable signups skew your numbers. Signup counts go up, but real usage doesn’t. Conversion rates and retention charts start to look off. If you’re running A/B tests, these fake accounts can flood your variants and make it harder to get a clean read on what’s working.
- They’re often linked to abuse: Many attacks start with account creation. Once inside, bots can spam other users, test stolen credit cards, or try to phish people. If your site becomes known for this kind of activity, users will start to notice and leave.
Where disposable emails come from
Disposable email services are easy to find and even easier to use. Most don’t ask for an account or any verification. You just visit the site, grab an address, and start receiving emails right away. Here are a few commonly used services:
- tempmailer.net
- tempinbox.xyz
- minutemailbox.com
- trashinbox.net
- spambox.xyz
- 1secmail.com
- luxusmail.org
- 10minutetempemail.com
Some sites rotate domains frequently to avoid detection, so the list changes over time.
Economics of disposable email services
These services aren’t running out of generosity. Most disposable email providers make money in one of two ways: ads or subscriptions.
Ads: The free inbox sites are usually packed with banner ads, popups, and affiliate links. The playbook is simple: get traffic from people trying to bypass signups, then monetize the clicks. It’s similar to what you see on temporary phone number sites.
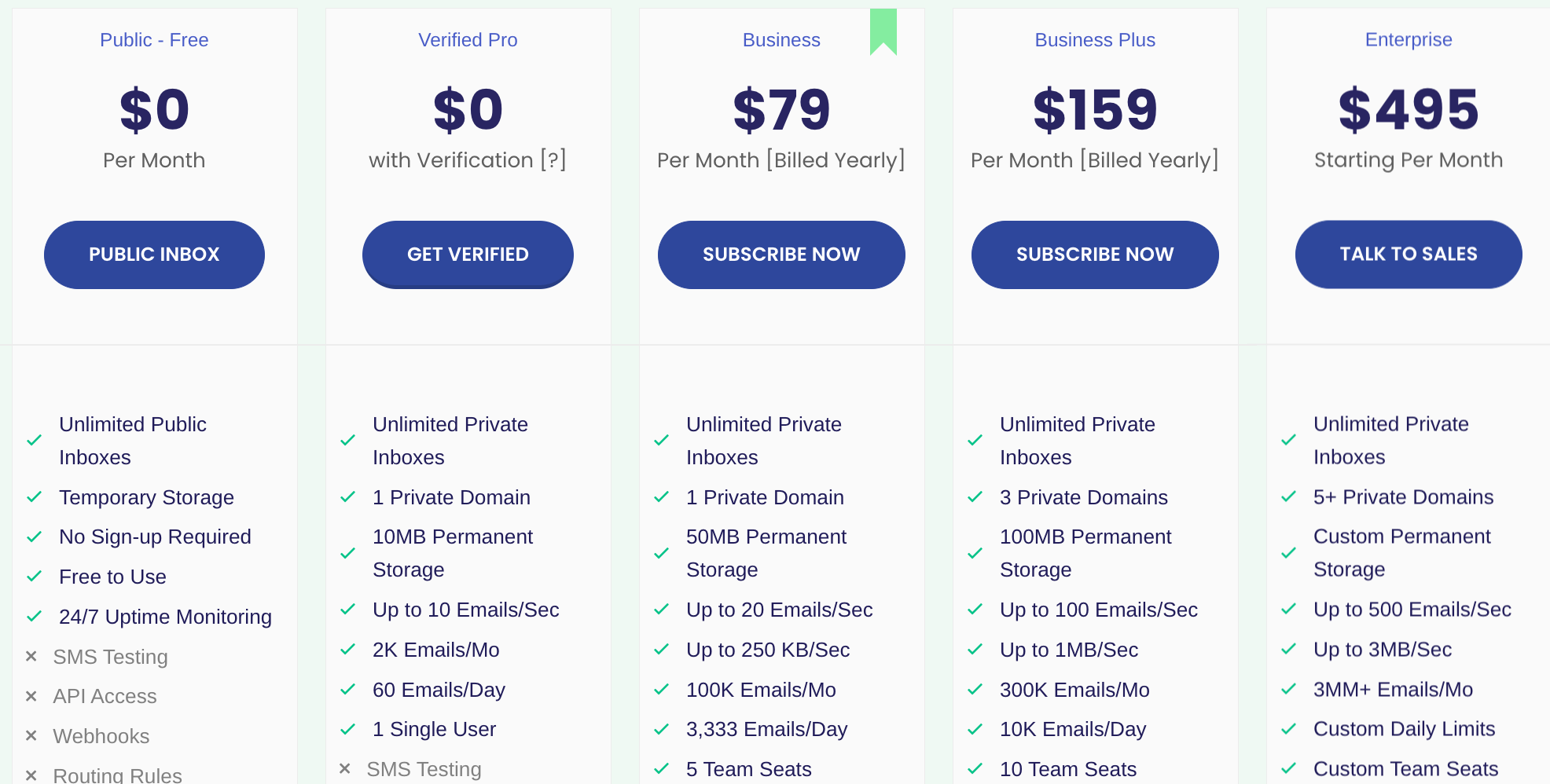
Paid plans: Some services offer premium features for developers or QA teams who need to test signups or email flows. Paid tiers might include things like custom domains, API access, or longer inbox lifespans. These plans are often marketed toward legit use cases, but attackers can use them too.
Using disposable emails with bots: a quick example
One common tactic attackers use when creating fake accounts is combining disposable email services with automated browsers. The idea is to fully automate the signup process—from generating the email to verifying it—without ever touching a real inbox or identity.
Here’s a simple Puppeteer script that loads a public inbox on Maildrop using a disposable address. No signup required. Just pick a username, and the inbox is available at https://maildrop.cc/inbox/?mailbox=<username>.
const puppeteer = require('puppeteer');
(async () => {
const browser = await puppeteer.launch();
const page = await browser.newPage();
await page.setUserAgent('Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/134.0.0.0 Safari/537.36');
await page.goto('https://maildrop.cc/inbox/?mailbox=thisatestforarticle');
await new Promise(resolve => setTimeout(resolve, 1000));
await page.screenshot({path: 'screenshot.png'});
await browser.close();
})();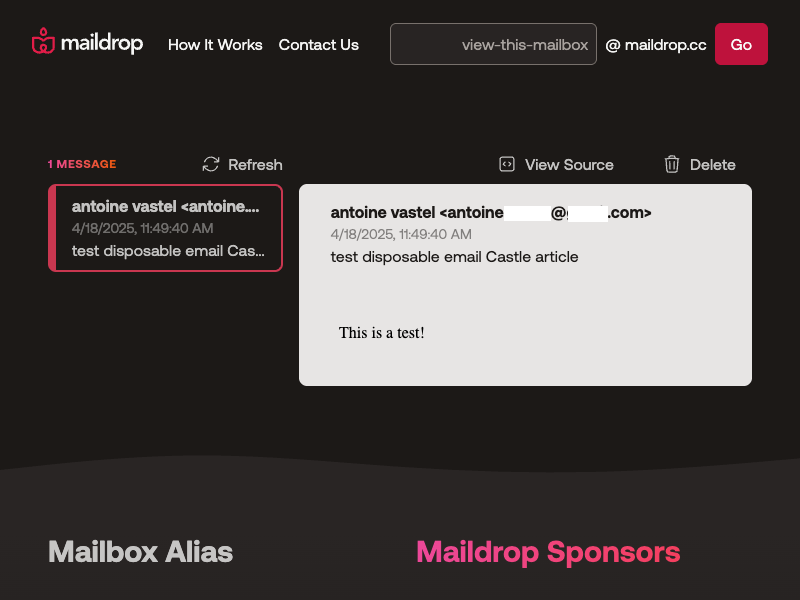
This script simply loads a Maildrop inbox and takes a screenshot, but it’s the foundation for something more powerful. Bots like this are often chained with other steps to fully automate fake account creation. For example:
- The bot generates or selects a disposable email address.
- It navigates to a target site’s signup page and fills out the form.
- If the site requires email verification, the bot polls the disposable inbox.
- Once the confirmation email arrives, it clicks the link to finalize the account.
This approach scales easily. With enough IP diversity and a queue of signup targets, an attacker can spin up thousands of fake accounts in minutes, each one verified and ready to use.
Some disposable email providers also expose APIs that make this process even cleaner, removing the need for browser automation entirely.
Not all disposable emails are malicious, and not all malicious emails are disposable
It’s easy to assume that every disposable email is used for abuse, but the reality is more nuanced. Some disposable services are built with privacy in mind, not fraud. They offer longer-lived inboxes, charge for usage, and don’t show up in open blocklists as often. That doesn’t make them safe by default, but the intent is different from the sites built to churn out inboxes for bots.
On the flip side, not all attackers rely on disposable domains. Plenty of them use free Gmail or Outlook accounts, which are harder to flag and more likely to pass filters. Some go further and register custom domains to avoid blocklists entirely.
So while blocking known disposable domains is useful, it’s not enough. Attackers will adapt. To catch them reliably, you need additional context, like IP reputation, device fingerprints, behavioral anomalies, and velocity signals. See more in our post on bot detection.
Should you block disposable emails?
In a lot of cases, yes, especially if you're offering something valuable at signup, like a free trial, credits, or access to a community. Blocking known disposable domains helps cut down on spam accounts, bots, and drive-by abuse.
But there are tradeoffs. Some legitimate users rely on disposable emails for privacy or to avoid marketing spam. If you block too aggressively, you might frustrate people who aren’t trying to game the system.
And as with most anti-abuse tactics, attackers will adapt. If your signup form blocks disposable domains, expect bots to fall back to using free provider accounts or domains they control.
So while filtering disposable emails is a good starting point, it shouldn’t be your only line of defense. Use it as part of a broader strategy—combine it with behavior signals, fingerprinting, and rate limits to make abuse harder without blocking real users by accident.
How Castle handles disposable emails
We don’t just block disposable emails. We treat them as early signals. Contextual, probabilistic, and often predictive.
Castle’s detection engine flags disposable email usage in real time. It’s not just a binary blocklist check. We map known disposable domains, but more importantly, we correlate usage with device fingerprints, IP reputation, behavior velocity, and entropy in signup flows. That’s where disposables show their real pattern.
Some customers choose to block these signups outright. Others use them as friction triggers, adding phone verification, throttling access, or isolating accounts from key flows.
For implementation details, check out our docs: Block signups with spam emails
Conclusion
Disposable emails are easy to get, hard to trace, and widely used, for both privacy and abuse. They help users avoid spam, but they’re also a go-to tool for attackers creating fake accounts, bypassing signup limits, or covering their tracks during fraud.
You can’t stop all bad signups by blocking disposable domains alone. But it’s a solid starting point, especially when combined with other signals like behavior patterns, device fingerprinting, and IP intelligence.
Castle gives you visibility into disposable email usage so you can take action where it matters: block accounts, flag suspicious traffic, or tune your onboarding flow to catch abuse without locking out real users.






