No matter your online activity, you don’t want your accounts taken over by someone else. You’d be unhappy to hear that someone logged into your BestBuy account to use your credit card to buy an 82” LED TV. You’d be upset if someone took over your Twitter account, posted spammy content, and then locked you out.
The bottom line? No one wants their online accounts taken over– and no company wants this to happen to their users. Even so, account takeovers happen. People find ways to gain access to account information so they can log into– and take over– user accounts.
Account takeovers happen in a series of stages. One not-so-great action leads to another. Soon enough, malicious activity is taking place. Users are hurt. They are inconvenienced, locked out of their accounts, and may experience substantial financial consequences. As a result, they lose trust in the company, which is damaging for your brand.
Today’s businesses are increasingly taking responsibility, as well as blame, for account takeovers. In the past, companies held users responsible. If a user’s password wasn’t strong, that was seen as their own fault. Thing is, today’s users expect that the online accounts they log into are secure and proactively protected.
That’s why, as a security leader at your company, you need to know what’s going on from that first credential scanning right up to the account abuse. You need to track things before your users get affected. You need to know what’s going on both outside and inside your applications. That’s why we’re sharing the 4 stages of account takeovers that you need to know.
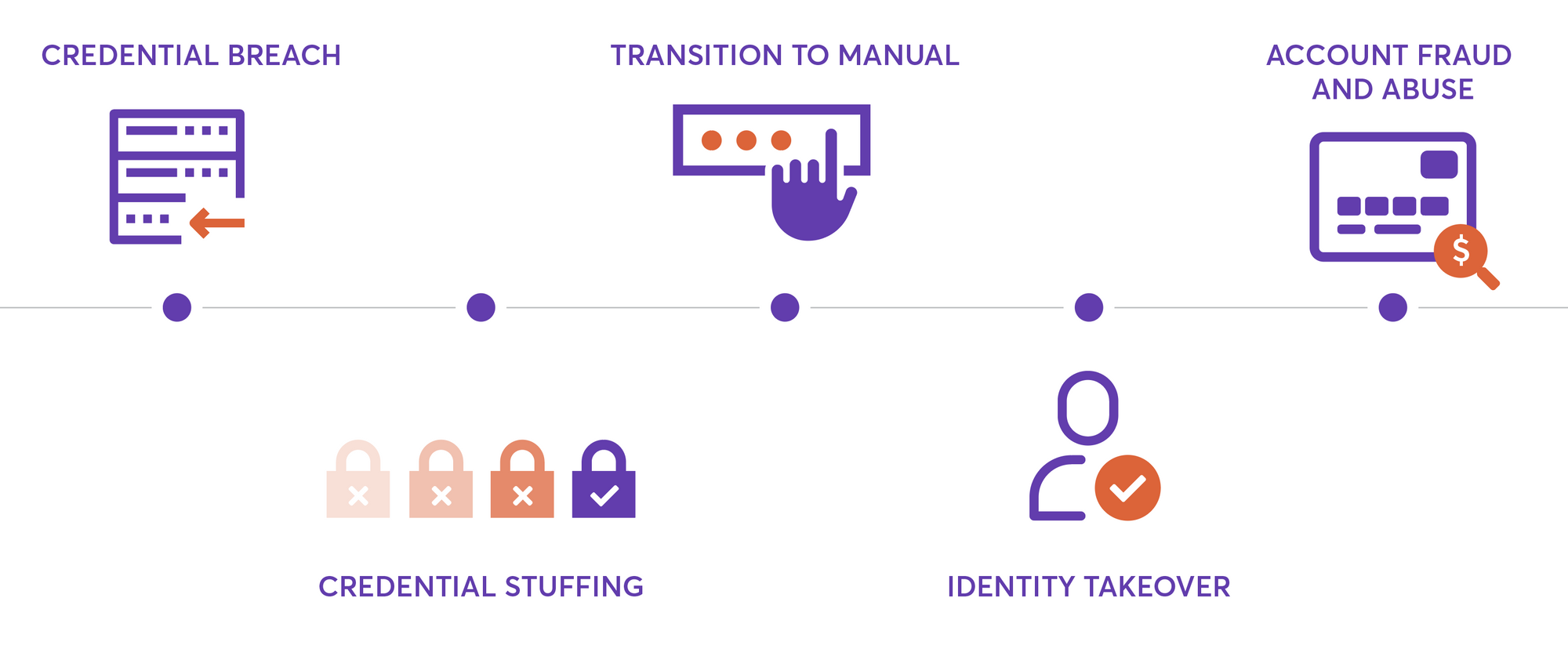
Before the takeover: Credential breach
Before an account takeover can happen, a credential breach has to occur. The credential breach is when a bad actor tries to circumvent existing security measures to access a company’s servers. Basically, this individual, or group of individuals, figures out a way to access as much data as they can.
For instance, if someone is able to access a major social media site’s database, they’ll have access to Tweets and stats about users, as well as usernames and passwords. The hacker can then take all those usernames and passwords and sell them somewhere on the dark web. Sooner or later, these leaks start circulating more publically, on open sites and forums such as Pastebin.
At the credential breach stage, the breach has only affected one business. However, if usernames and passwords have been leaked and circulated, they can be used on other sites, leading to account takeovers.
Stage #1: Credential stuffing
A credential breach might not be such a large issue if people did not use the same usernames and passwords on many sites. Password managers are amazingly simple and powerful tools to prevent this, and we heavily encourage using them! But the reality is, the vast majority of the internet uses the same password over and over again. Because of this, one credential breach can result in subsequent malicious activity across a range of sites and apps.
Credential stuffing is when automated bots test leaked credentials on others sites to check which ones are valid. For example, they might take an entire database of username and passwords and test it on another site to see if the credentials match up. From there, they’d be able to create a new list of accounts which are validated for a particular site. This process– going from a huge list of random, somewhat invaluable credentials to a list of highly valuable harvested accounts– is often called account harvesting.
Bot detection solutions can detect when someone is doing credential stuffing, which is helpful to any security team trying to protect user accounts. These alerts are extremely valuable, though they don’t often provide insights or history into which specific accounts were actually targeted or compromised. As a result, the user might be left in the dark that their credentials are in the hands of an attacker. Bot and perimeter detection solutions perform best when they’re used alongside solutions that provide visibility into individual user behavior, and highlight the user accounts that are being targeted.
Stage #2: Transition to manual
In stage #2, account takeover transitions from a matter of stolen credentials to a situation where a human (or sometimes a bot) uses leaked credentials to log in to accounts, one by one, and extract value. After credentials have been verified in stage #1, they’re then sold on forums, so it’s many times a different actor coming back in stage #2.
For example, someone might buy a list of verified accounts for a certain amount, reasoning that they’ll be able to withdraw more funds by logging in. They can use any laptop or home computer to log into sites via a standard web browser like Safari or Chrome. Suddenly, they’re in the account. Obviously, this is bad news.
Fraud protection solutions have gotten incredibly good at detecting actual fraudulent purchases, which helps to flag suspicious financial transactions as soon as they happen. However, it’s difficult to detect this prior to the transaction, like when someone initially logs into an account. As a result, this “transition to manual” stage is often a blind spot for many companies, resulting in a series of fraud chargebacks or review queues only identified at the point of purchase.
Stage #3: Identity takeover
At this point in the process, the hacker can do what they want with the account because they have control over it. They can change email addresses, shipping addresses, bank account numbers, and alter other personal information.
Changing this information allows the hacker to gain what they want from the account. For example, they might change a shipping address so that all the products bought are shipped to them. They might change the bank account so that they can transfer any account funds to themselves.
The whole secret here is that these individuals want to use the account as if the account owner still has control. They’re careful not to do anything suspicious. However, if a company has a record of user activity, and is able to identify something abnormal (such as an odd location, device, or rare time of day), they can alert the user to determine whether their account has been taken over.
Stage #4 Account fraud and abuse
At this stage, the account is used for truly malicious activity and is abused. The hacker can now make purchases, ship themselves goods, or commit some other form of abuse. In this final stage, the hacker is executing on their plan.
Unfortunately, once the abuse happens, it’s often too late. At this point, you’re left trying to detect theft or fraud after it’s already happened, as opposed to detecting a threat the moment account information is changed, or even when the first anomalous login occurred.
Even if an account takeover occurs and no fraud is detected, the user is vulnerable. Sometimes, fraudulent activity can happen offline after making online changes (such as an individual going to a brick-and-mortar store to purchase smartphones). Sometimes, the fraudulent activity happens much later.
Protecting your users from account takeovers
Security remains a confusing subject to users and complex for businesses that serve them. That’s why understanding the lifecycle of account takeover is so essential. By having a firm grasp on how account takeovers happen, you’ll be better positioned to take steps to mitigate risk at each and every stage throughout your applications.






