This is the first article of a series about anti-detect browsers. In this article, we provide an overview of anti-detect browsers and their main features. We also present the most common fraudulent use cases of these browsers. In the next articles, we’ll deep dive into the techniques they use to forge fingerprints, and how we can still try to detect them
Before we jump into the anti-detect browsers, let’s do a quick reminder about bot and fraud detection. Most websites that operate at scale have systems in place to detect fraudsters and bad bots trying to abuse their service. For example, banks have security mechanisms to ensure that even when someone has a correct login and password, it’s the actual owner of the account trying to log in and not someone who stole the credentials through a phishing campaign. Similarly, social networks like TikTok and Linkedin have different security mechanisms to prevent the creation of fake accounts that could be used for spam.
These anti-fraud and anti-bot security systems often rely on device fingerprinting, a technique that leverages information about the user device and browser, such as the screen resolution, the type of GPU as well as the timezone, to track users, even when they delete their session cookie or change their IP address.
What Are Anti-Detect Browsers?
Anti-detect browsers are specialized browsers designed to bypass these security mechanisms by making it easy for their users to modify their device fingerprints. They achieve this by altering various signals commonly used for device fingerprinting, such as:
- The user-agent string;
- Information about the device GPU (webGL renderer, webGPU API);
- The timezone and the screen resolution;
- Characteristics about the machine like the number of CPU cores and the amount of RAM.
As we can see in the screenshots below, taken from two anti-detect browser websites, they also offer features to spoof advanced fingerprinting signals such as WebGL fingerprinting, canvas fingerprinting, and audio fingerprinting.
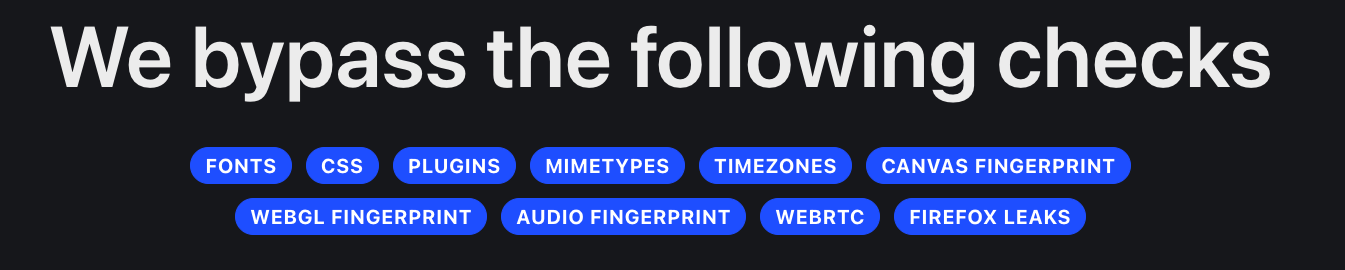
Thus, it makes it difficult for online platforms to link multiple sessions to the same user. Unlike regular browsers, which maintain a consistent fingerprint across sessions, anti-detect browsers allow users to generate unique and varied fingerprints to remain anonymous or appear as different users.
As we can see in the screenshot below, they make it easy for users to change different attributes related to their device fingerprints.
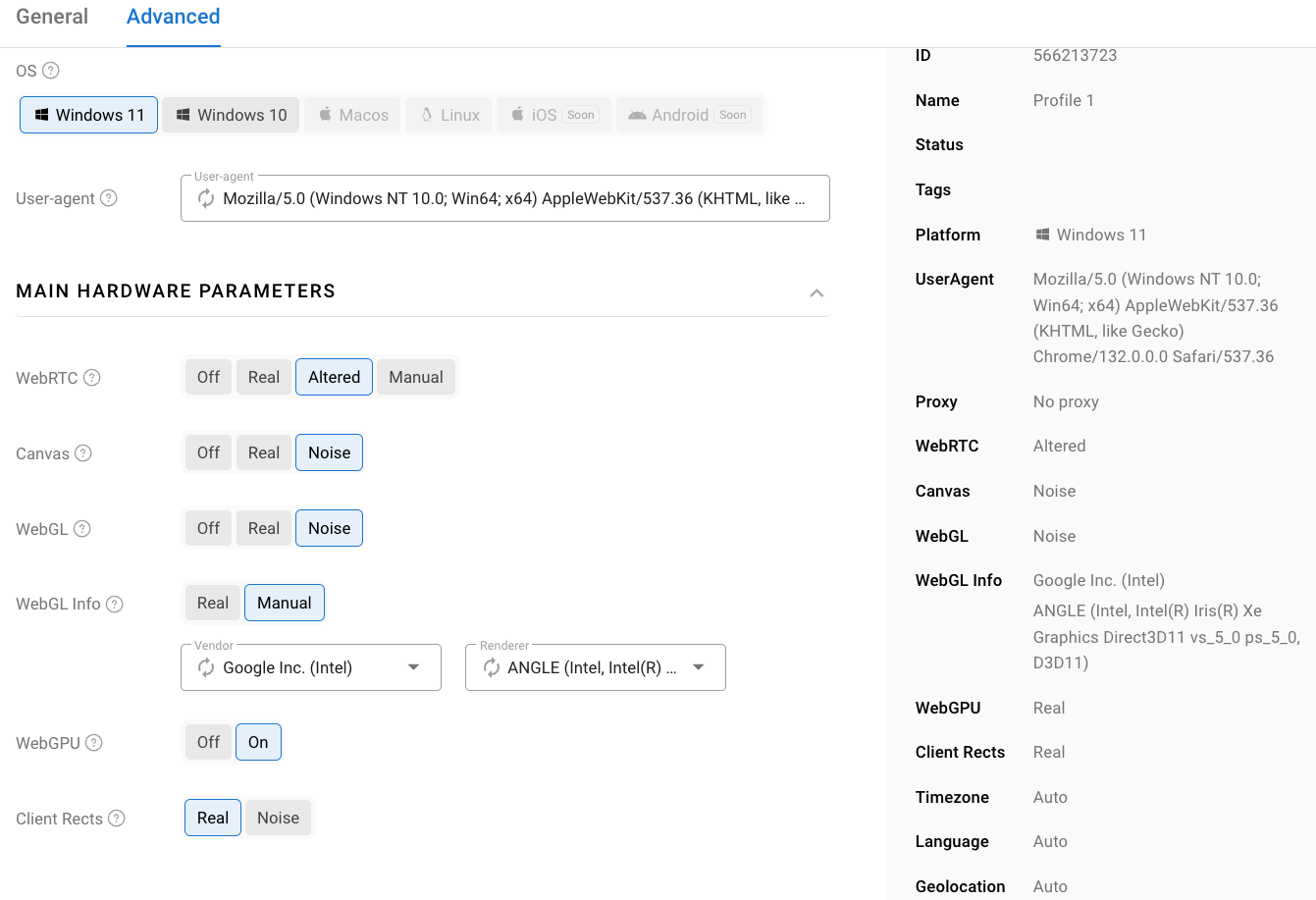
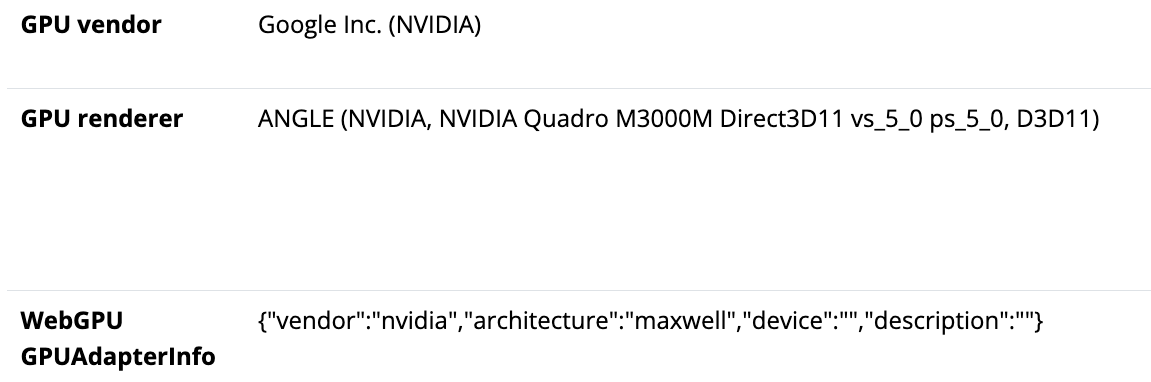
Crafting consistent device fingerprint: Anti-detect browsers ensure the generated fingerprints are consistent. In the previous screenshot, we chose a WebGL renderer linked to Nvidia, even though our real renderer is “ANGLE (Apple, ANGLE Metal Renderer: Apple M4 Pro, Unspecified Version)”. When we do this, the anti-detect browser automatically updates all attributes related to the webGL renderer, such as the webGPU adapter so that all values are consistent. Thus, when we analyze the modified fingerprint, we see that all values mention an NVIDIA GPU.
Proxy and VPN Integration: While device fingerprinting is a key element of most anti-fraud and anti-bot systems, another important signal is the IP address. Indeed, most security systems leverage information related to the IP address to detect potential fraud. For example, if a user makes too many requests from the same IP address, he may get banned. When it comes to account security, websites may also ask for a second authentication factor if the password is correct but the user is trying to log in from an IP address from a different country as usual. Thus, all anti-detect browsers natively support proxies and VPNs, which enable their users not to reveal their real IP address by using different IP addresses over time.
Multiple Profiles Management: Finally, one of the key features of anti-detect browsers is the notion of profile. Users can create and manage multiple virtual browser profiles, each with a unique fingerprint, enabling them to run multiple accounts simultaneously. Each browser session operates in a separate environment, preventing tracking mechanisms from linking sessions together.
Thus, from the website point of view, each user has a stable and consistent fingerprint over time, and their session cookies are not shared
Bot automation integration: While in the past, anti-detect browsers were mostly used manually, most of them offer integration with popular bot frameworks such as Puppeteer and Selenium to automate them with bots.
What Are Anti-Detect Browsers Used For?
Anti-detect browsers are used for various purposes, both legitimate and illicit. Digital marketers and e-commerce professionals often use them to manage multiple accounts on platforms such as Facebook, Google, and Amazon without being flagged for suspicious activity.
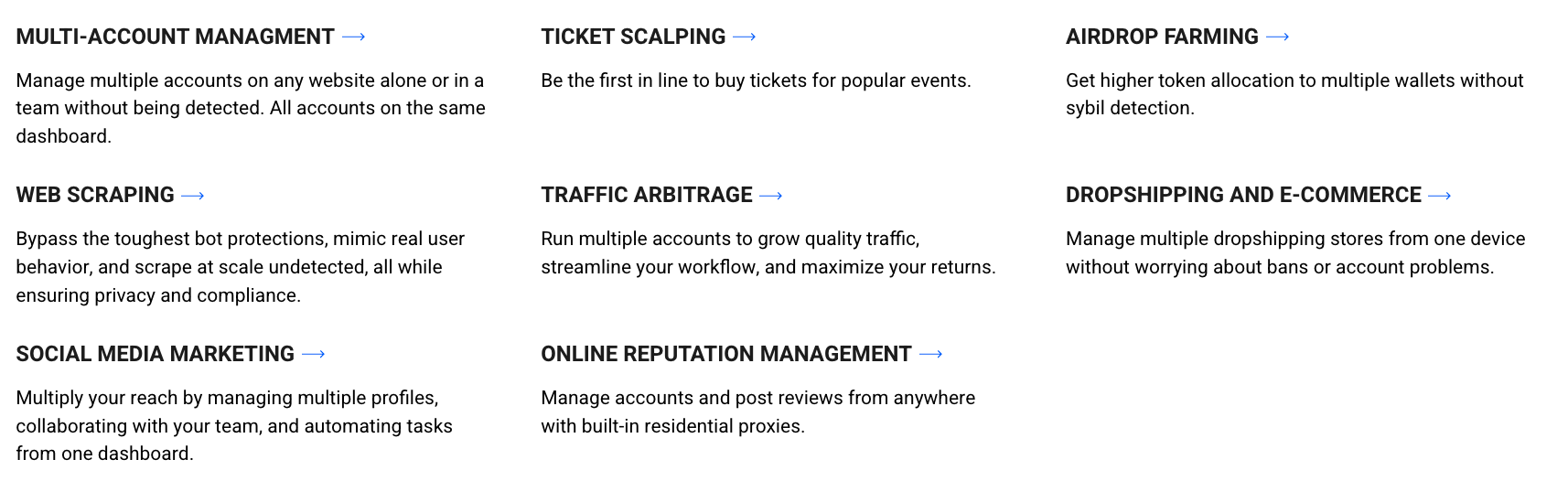
However, while most anti-detect browser companies emphasize privacy and marketing automation use cases, there is nothing to prevent their users from conducting malicious activities, such as carding, fake account creation, and account takeover.
Focus On Malicious Use Cases
Since anti-detect browsers enable fraudsters and bots to modify key signals used by anti-fraud systems, such as device fingerprints and IP addresses with proxies, they can be used to conduct several types of attacks, such as :
- Account Takeover: With access to stolen credentials, fraudsters use anti-detect browsers to impersonate legitimate users, bypass security measures, and hijack online accounts. Once inside, they can change shipping addresses, withdraw funds, or make unauthorized purchases—all while appearing as the original account holder.
- Creating Fake Accounts: Fraudsters exploit anti-detect browsers to generate multiple fake accounts, often to take advantage of promotional offers, abuse free tiers, and post fake online reviews.
- Bot-Driven Engagement: Threat actors use anti-detect browsers to automate fake likes, comments, and shares to manipulate platform algorithms. The same technique can be used to spread misinformation on social networks.
- Affiliate Program Abuse: Fraudsters simulate referral traffic and conversions using multiple virtual identities to exploit commission-based programs.
- Subscription Fraud: Fraudsters use stolen payment details to create multiple accounts and resell access to premium streaming services.
- Credential Sharing Abuse: Malicious users automate the sharing and resale of account credentials, violating fair-use policies.
Bypassing Risk-Based Authentication: Anti-detect browsers are particularly good at conducting account takeover. Indeed, most sensitive websites like banks and cryptocurrency platforms use a risk-based authentication system. When a user logs in, they don’t only check the correctness of the user/password combination. They also verify if the user is connecting from a known IP or a known, if it’s a known device using a cookie and a device fingerprint. If someone is suspicious, they may ask for a second authentication factor or block the connection.
Thus, fraudsters started to collect the device fingerprints of their victims in addition to their credentials. Whether it is using an info stealer or on a phishing page, when they steal the victim’s password, they also collect fingerprinting information about the user's device, such as his screen resolution, his GPU model, and his timezone. Thus, when fraudsters sell stolen credentials, they also sell the associated device fingerprint.
Once in possession of the stolen credentials and the device fingerprint, they can use an anti-detect browser to:
- Forge the device fingerprint to be the same as the victim;
- Use a residential proxy within the anti-detect browser to have a clean IP address located in the same country as the victim.
Thus, they minimize their chance of being detected by risk-based authentication systems.
Can Anti-Detect Browsers Be Detected?
There are no silver bullets when it comes to detecting these browsers. Indeed, they use different techniques to escape detection. Thus, it’s key to use a multi-layered approach to add redundancy in the detection.
Indeed, while most of the naive fingerprint spoofer software applies fingerprint lies at the JavaScript level, which can be more easily detected due to side effects, anti-detect browsers often recompile Chromium browsers and lie at a lower level. Thus, they have less detectable side effects.
Detecting fingerprint inconsistencies: Another common source of detection comes from inconsistent fingerprinting attributes. This can happen when different attributes of a fingerprinting whose value should be correlated start to diverge. For example, someone whose GPU renderer would indicate a Mac M4 but whose user agent string would indicate Windows. However, most anti-detect browsers leverage real-world device fingerprints to ensure the values are consistent. They also raise warnings when users try to lie about attributes that could be detected, e.g. if they are too far from their real configuration.
Thus, detecting anti-detect browsers requires detecting as many fingerprinting signals as possible, and also to correlate the values of each signal with each other to ensure their consistency.
Detecting canvas randomization: Since most anti-detect browsers tend to lie about canvas and audio fingerprinting, it’s also key to have JavaScript signals capable of detecting altered values. We discuss more about forged canvas fingerprinting detection in this other blog post.
Red pills and dynamic proof of works: Moreover, it’s key to have a fingerprint that leverages advanced red pills and proof of works to detect lies in the underlying device fingerprint. The fingerprint shouldn’t trust the values returned by the browser, instead, it should also infer the real device characteristics by asking the browser to execute specific information. For example, it is possible to infer the real nature of the user OS using canvas fingerprinting and font enumeration.
In addition to detecting the anti-detect browsers themselves, it’s key to leverage all available signals. Thus, it’s important to detect
- If the user is connecting from a proxy IP;
- If the user behavior is linked to human activity or if it’s automated with a bot;
- When it comes to fake account creation, you can also detect disposable emails and temporary phone numbers
Conclusion
Anti-detect browsers are specialized tools designed to bypass security mechanisms by allowing users to modify their device fingerprints. Their main features include:
- The ability to modify fingerprinting signals like user-agent strings, GPU information, and system characteristics
- Profile management capabilities that enable users to maintain multiple distinct virtual identities
- Built-in proxy and VPN support to mask IP addresses
- Integration with bot automation frameworks
While these browsers have legitimate uses in marketing and e-commerce, they can also enable malicious activities such as account takeover, fake account creation, and subscription fraud.
Detection of these browsers is challenging because they:
- Implement fingerprint modifications at a lower level, reducing detectable side effects
- Use real-world device fingerprints to maintain consistency
Effective detection requires comprehensive fingerprinting signals, correlation between different signals, and the use of advanced techniques to verify the authenticity of device characteristics.






