A few years ago, Puppeteer stealth was one of the most popular tools in the automation and scraping ecosystem. Built as a plugin system on top of Puppeteer, it made automated browsers harder to detect by patching obvious fingerprinting artifacts. It also shipped with convenience plugins like ad blockers and integrations with CAPTCHA farms, which made it attractive to both scraper developers and fraud operators, for example, the Open Bullet 2 credential stuffing software uses a C# port of Puppeteer Stealth under the hood.
Its popularity is reflected in its GitHub repository, which has accumulated around 7,000 stars. The growth was steady for years and is still inching upward today, although the trend has started to plateau.
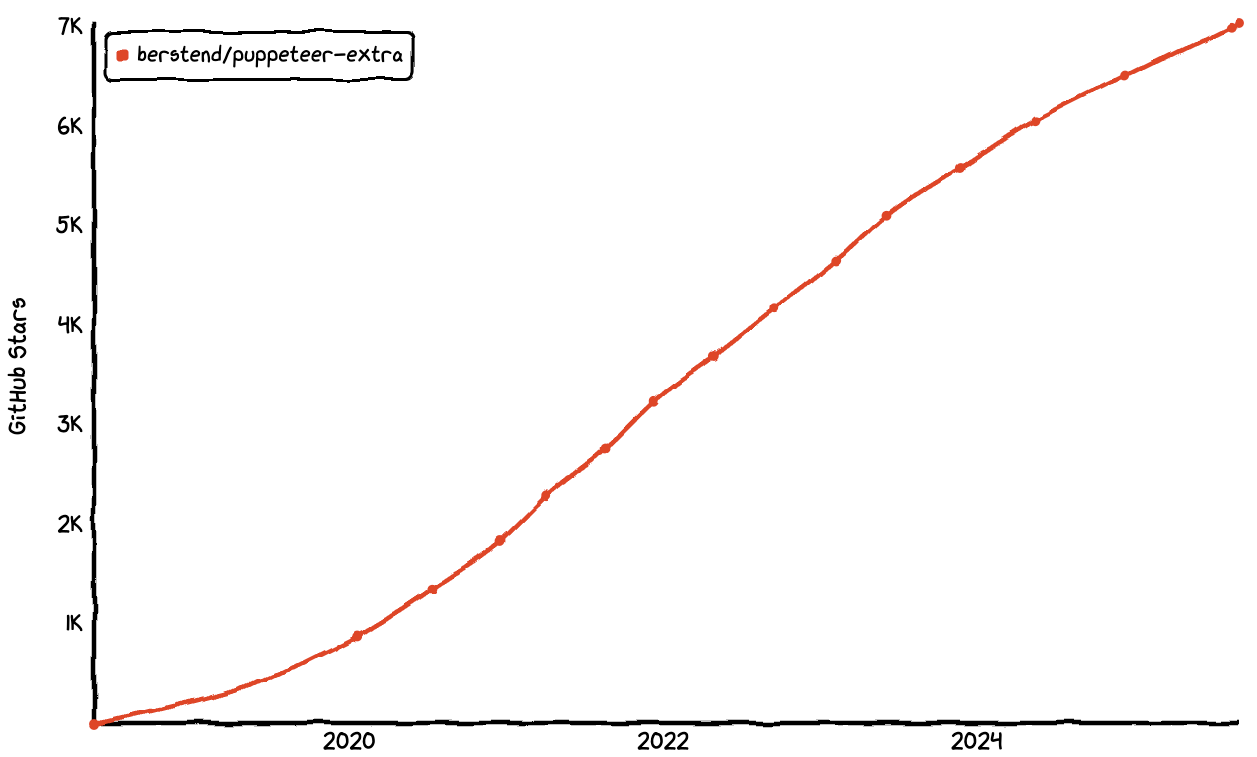
Despite this enduring interest, the project itself hasn’t been actively maintained for years. Today, GitHub issues are filled with developers reporting that Puppeteer stealth is detected by most modern defenses.
Meanwhile, the anti-detect landscape has evolved. With the release of a more realistic Headless Chrome, attackers started shifting to newer frameworks like nodriver or Rebrowser patches, which focus on removing subtle Chrome DevTools Protocol (CDP) side effects instead of injecting lies at the JavaScript level.
This raises the question: is Puppeteer stealth still relevant in 2025, or has it been left behind?
What our data shows about Puppeteer stealth usage in 2025
For the purpose of this analysis, it wasn’t enough to simply detect automated browsers in general. We needed a signal capable of identifying Puppeteer stealth specifically, and distinguishing it from other frameworks like vanilla Puppeteer or Playwright. That’s what allowed us to measure how much Puppeteer stealth is still used in the wild. While we don’t go into the details of this signal, our CastleJS library implements a signal that enables us to uniquely identify Puppeteer stealth due to its side effects.
Looking at 30 days of traffic in October 2025, we observed around 205,648 events linked to Puppeteer stealth.
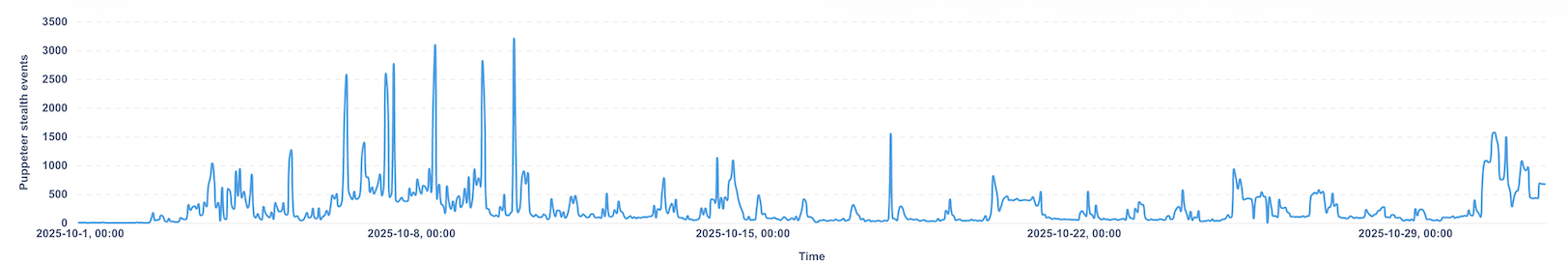
A few things stand out from the data:
- The activity was concentrated on a small number of customers rather than spread evenly.
- The main attack types were credential stuffing, fake account creation, and some spam activity.
- By comparison, during the same period, we detected roughly 10 times more traffic from vanilla Selenium bots.
So while Puppeteer stealth is still present in production traffic, it no longer dominates. For defenders, the takeaway is clear: it remains worth detecting, but the bigger threats today come from other frameworks and simpler automation tools.
Still worth detecting, but no longer the main threat
Puppeteer stealth isn’t dead, but it’s past its peak. Attackers still use it, and we continue to see it in credential stuffing and fake account activity, but the volume is modest compared to other frameworks.
For defenders, this means two things:






