Blog #2 in a 4 Blog Series on Attack Tactics that Increase Success Rates for Account Takeover… And What You Can Do to Thwart Them
“Won’t you be my neighbor?” said Mr. Fred Rogers.
It’s a powerful, inclusive refrain from the popular U.S. tv show Mr. Rogers’ Neighborhood. It’s theory is that neighbors are part of our community – they are simply friends we may not have met yet.
This is the key to the second tactic in our four-part blog series on account takeover attack methods and mitigation capabilities. You can read the first blog in the series here: How Attackers Hide In Plain Sight When Perpetrating Account Takeover Attacks
Tactic #2: Appearing Local
If attackers can trick us into thinking they are our neighbors (and potential friends), maybe we will cut them some slack when they do something suspicious. They are counting on it, which is why they have increasingly started using local IPs. If they can appear to come from a nearby location, they hope to be able to operate more freely.
It is no secret that IPs from some locales immediately arouse suspicion. A quick Google search will confirm that IPs from Brazil, China, Germany, Iran, Italy, The Netherlands, Russia, Thailand, Ukraine, and Vietnam top the list of countries where large numbers of cybersecurity threats originate.
Castle’s own research on the distribution of attack IP origins over the past two years, which is depicted in the graph below, validates why traffic from certain countries warrants being flagged and monitored more rigorously.
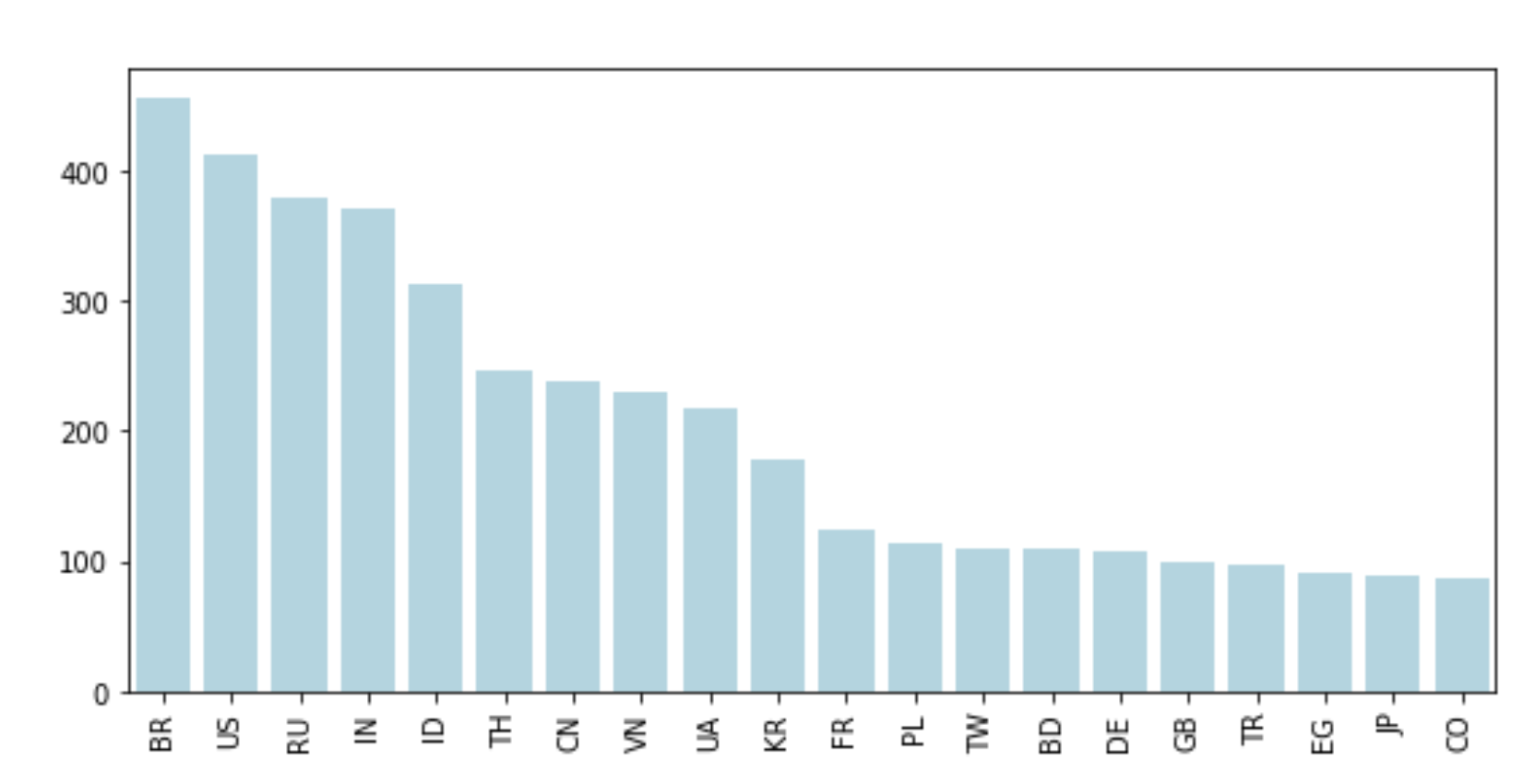
The takeaway is that if attackers can launch their traffic in countries and locations that raise less suspicion, they have a better chance of hiding their activities. It also helps them subvert measures that may be in place on the site, such as geo blocking, which is designed to stop certain credential stuffing attacks.
For example, a service that requires a U.S. social security number to sign up, may be set up to automatically block any user coming from a non-U.S. IP address. So, if attackers can use a U.S. address, they will be able to circumvent this mechanism. (By the way, this defensive approach is not recommended given it is not precise enough and will likely end up frustrating more customers than it protects).
The Role Proxies Play
There are really two ways attackers can gain access to local IPs they can use in their account takeover attacks:
- Data center proxies: provided by hosting companies, such as Amazon and Azure. These providers enable companies/users to select their physical location when buying server capacity, which helps them ensure it is as close as possible to their end users to reduce latency and improve overall performance. It is also enables companies to adhere to regulatory requirements, such as those introduced by the European Union’s General Data Protection Regulation (GDPR), that require data remain within specific borders or regions.
- Residential proxies: provided by residential IP providers, such as Luminati and Oxylabs. These providers assign IPs for personal home use, offering users a pool of IPs to choose from, which belong to regular personal Internet providers, such as Comcast and AT&T. This allows an attacker to select the location they want their IPs to be in and rotate them as needed.
There are methods for detecting and blocking datacenter proxies (discussed next), so using a number of residential proxies further increases the chances the attacker will be able to blend into normal traffic. It also helps them trick the target website into thinking they are a normal user accessing it, so they can hide their activity and evade detection.
The ability to choose where server capacity is located enables attackers to launch their traffic from different locales. This helps them better mimic the activity of real users and reduce the chance they will be blocked by methods set up to detect and block datacenter proxies, such as geo blocking and lists of datacenter IPs available as open source such as the IPCat project and there are several other databases available through commercial vendors.
Real-World Example
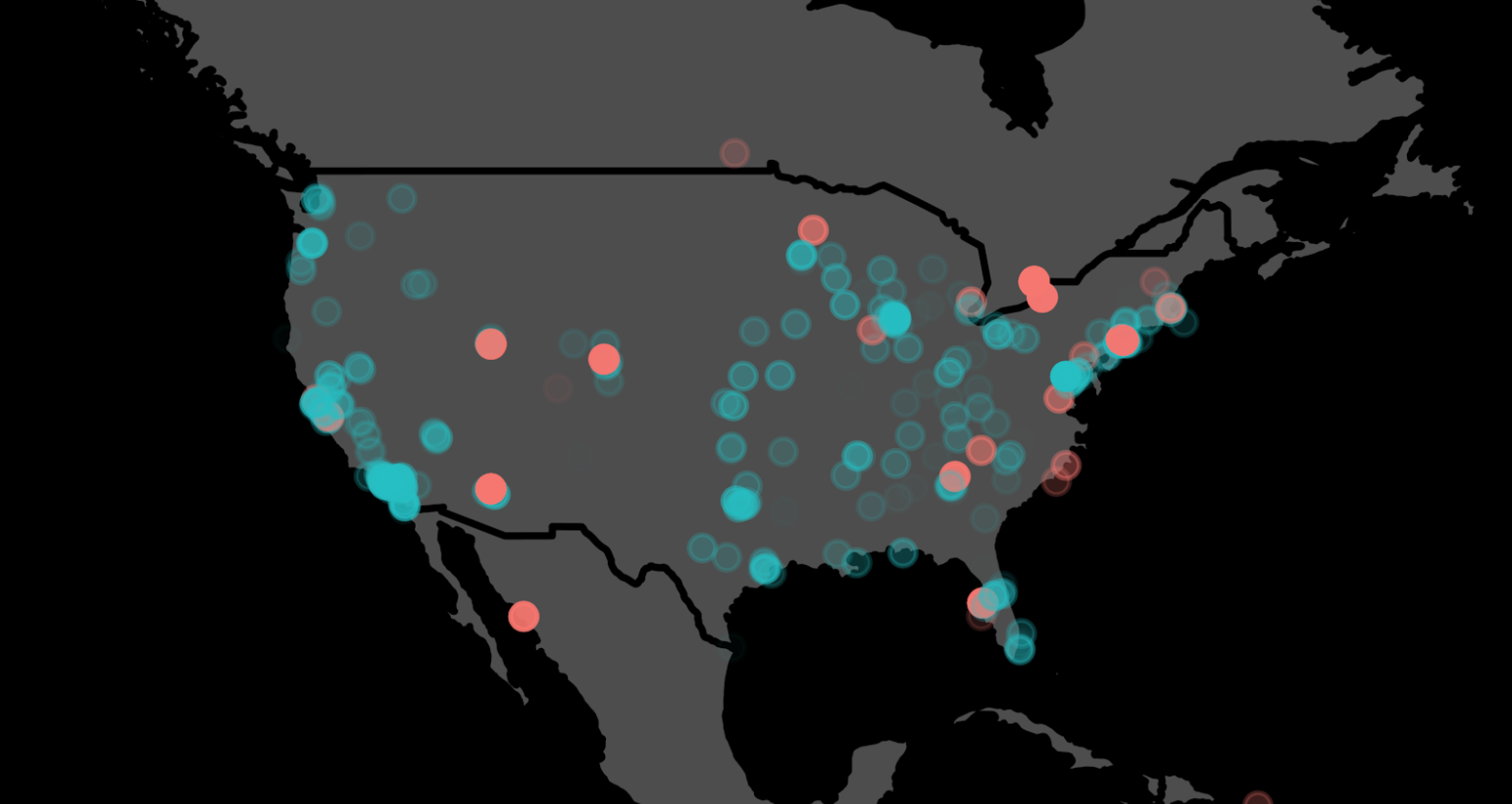
For example, the attack depicted below used 1000 IPs from multiple data centers across the U.S. (indicated by the red dots) to blend in with regular traffic (blue dots). Over a 10-hour period, they attempted 650K logins, which wouldn’t have raised much suspicion at all and probably would have gone undetected, if Castle hadn’t been protecting the site.
Video Demonstration
Watch this quick 1-minute video that shows the progress of an account takeover attack that uses 907 IPs, from 21 different ISPs, in just two countries. The attacker targeted a total of 36,814 users with 667,247 login attempts that would have gotten 1056 valid credentials had Castle not stopped it.
The Answer?
Because attackers are using local IPs, traditional geo blacklisting and manual blocking isn’t going to help. It takes finesse and sophisticated technologies (because it’s not practical to rely on manual intervention) to prevent account takeover from these types of attacks. Look for solutions that can:
- Decipher suspicious traffic from normal traffic patterns
- Understand user and device behavior
- Automatically block malicious activity
For more information about Castle's customer identity and access management capabilities or to start a free trial, please go to https://castle.io/.







