As the use of online businesses and services has increased in the last few years, so has the amount of fraud. In fact, online fraud has grown a staggering 149% so far this year (highlighted in this report by Transunion). While online businesses and services have risen to the challenge of increased demand, many have not kept up with the rise in fraud. Fraud is typically committed with a false or stolen identity. By detecting bad identities in each stage of the customer journey (signup, login, during key activities), overall fraud can be reduced.
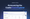
Today, Castle is releasing the Event Explorer, giving security and fraud teams a new way to discover and investigate malicious activity. Calls to the Castle /authenticate, /risk, /filter and /log APIs generate data that is stored as events. The Event Explorer exposes this data, giving you a single place to go for complex investigations and ad-hoc exploration. Also, unique to Castle is the ability to jump from an event into the user object related to that event.
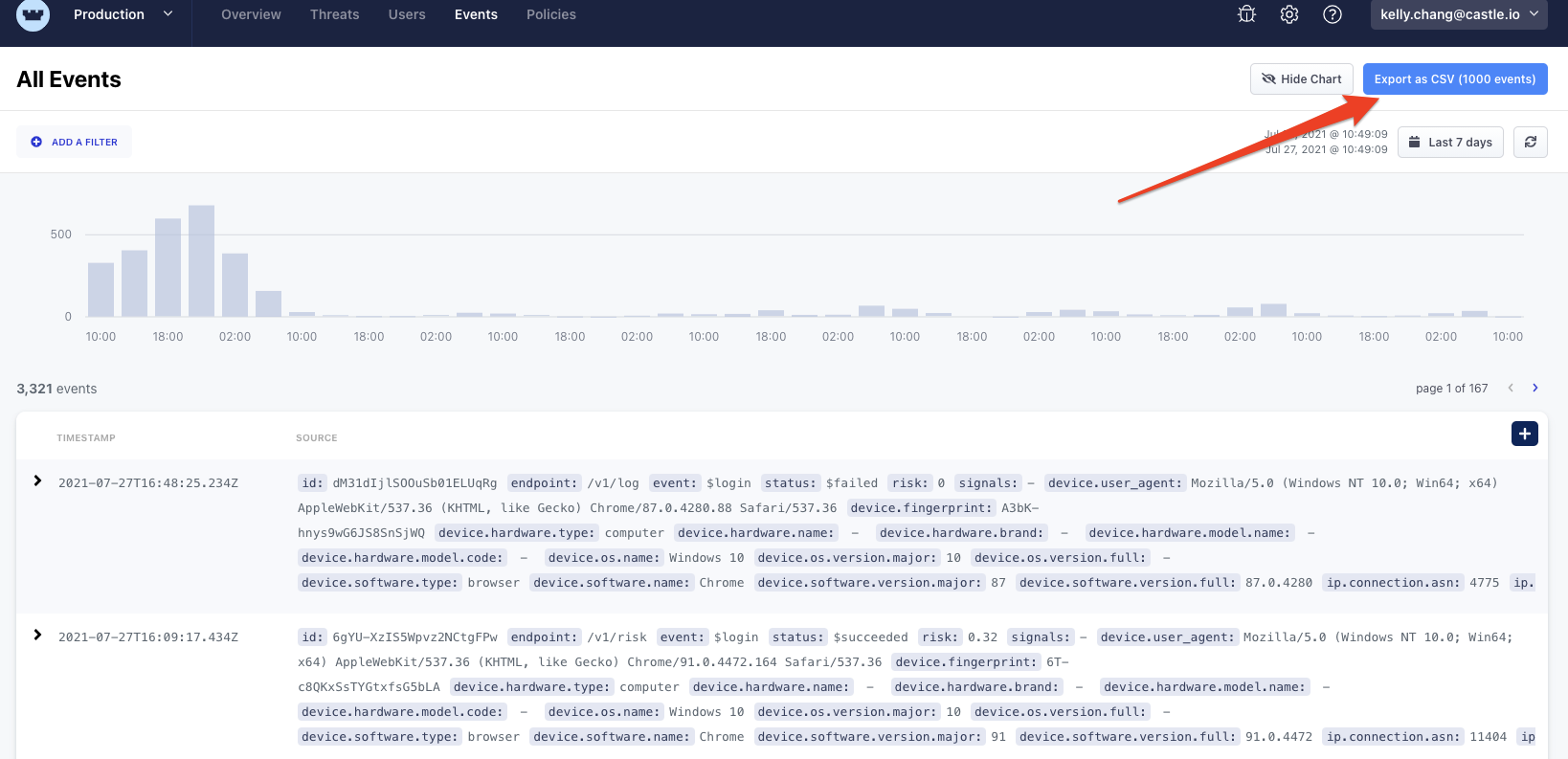
Using the query capability of the Event Explorer, you can narrow down the set of events based on key/value pairs that are relevant to malicious activity, such as an IP address, browser type or email address. Event sets can be exported to CSV, making them easy to share.
Prior to the Event Explorer, teams had to patch data together from multiple sources. Now, that data is available in one place, making it faster and easier to investigate malicious activity. Security and fraud teams have one place to go to find patterns of malicious activity and investigate specific incidents.
The Castle Event Explorer:
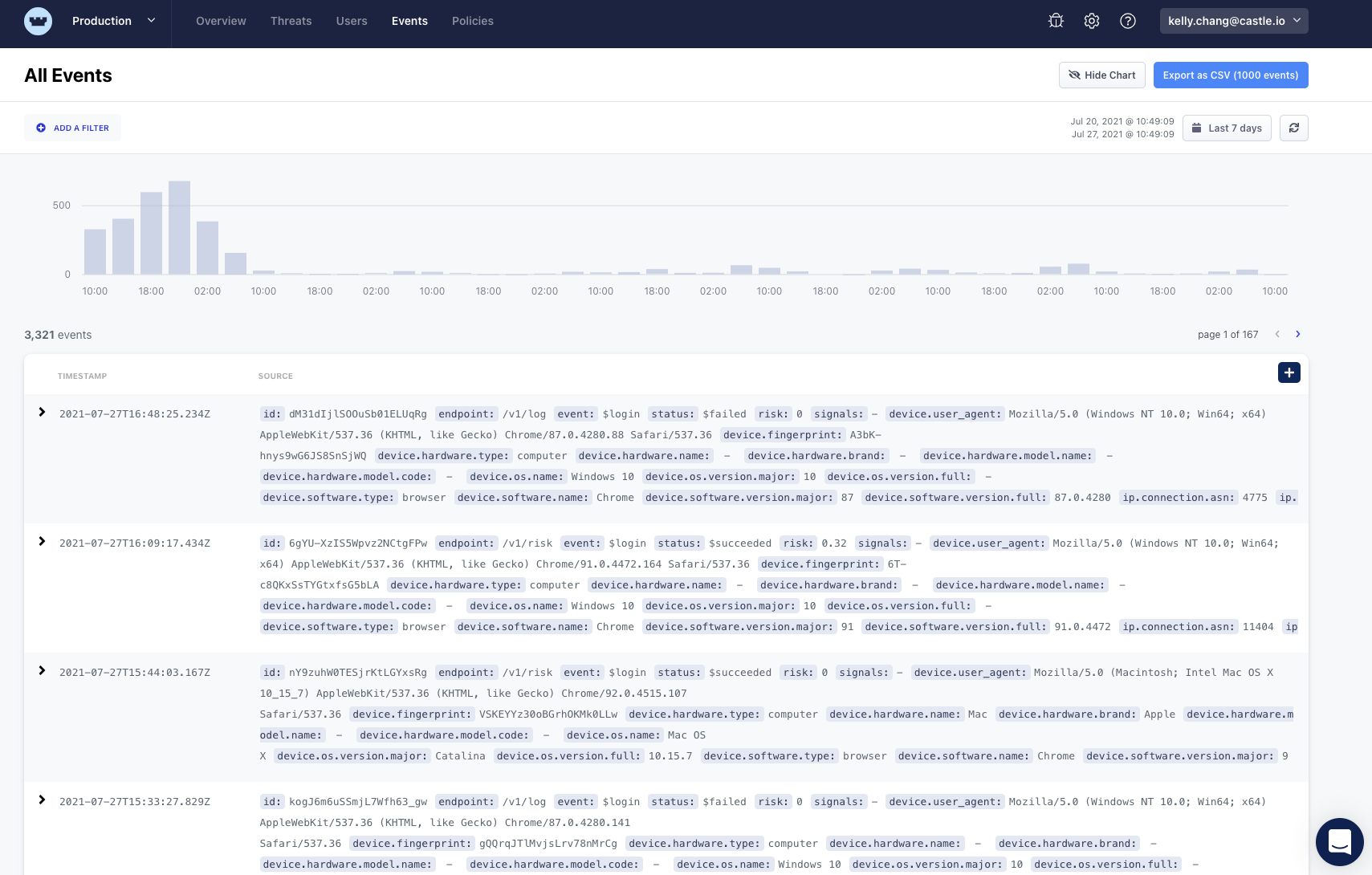
Events can be filtered based on key/value pairs:
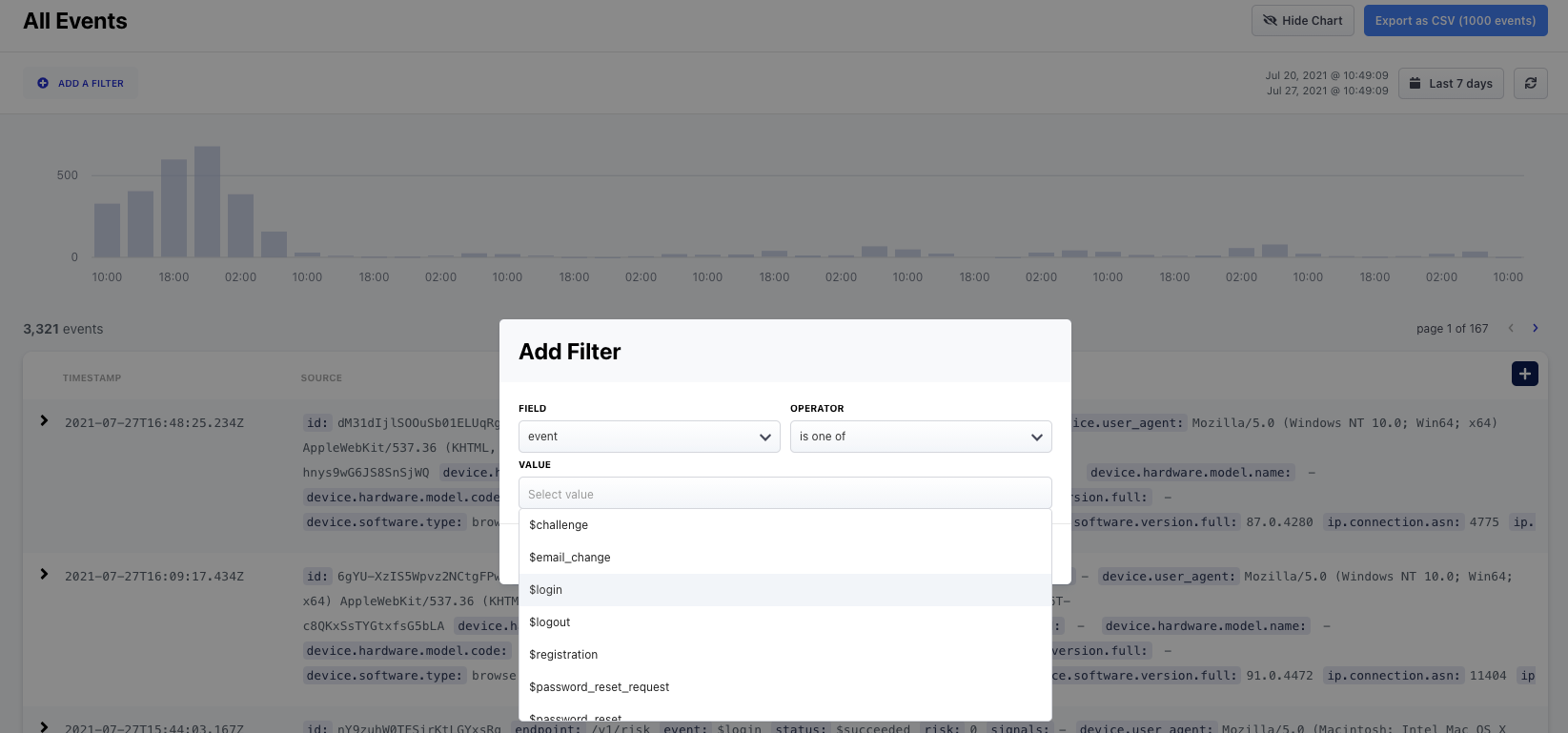
Choose what keys are shown:
Export the data in CSV format to share or analyze offline:
With the Event Explorer, Castle is a much more powerful tool for discovering and investigating. You can see a short demo of the new Event Explore below.
Sign up here to try Castle for free, or reach out for a demo if you’d like to hear more!