Automating account verification has become the norm for businesses to minimize fraud and validate legitimate users online. However, it's not always clear how verification helps with different types of fraud while striking a balance between security and privacy, yet also avoiding unnecessary friction
In this article, I'll explore common options for account verification and assess their effectiveness against three classes of fraud/abuse problems:
- Bots and automation: Automated software mimicking human behavior for the purpose of performing abuse at scale, e.g., fake account creation or spam comments.
- Account takeover: Unauthorized access to a user's online account, either by using stolen credentials or performing credential/brute force attacks. Excludes attacks created by scripts or automation for a clear separation from problem 1.
- Service abuse: Misusing or overusing online services for personal gain or malicious purposes, such as spamming or scamming other users on the platform. This excludes abuse caused by scripts or automation in this definition.
The verification options used in the comparison are limited to those that are easily available and don't require users to enroll, such as with OTP codes.
It's worth noting that for these three types of fraud problems, the practical level of protection ultimately depends on the type of service provided. For example, banking and crypto–often with greater risks of monetary loss–fall prey to more sophisticated and costly attacks such as SIM swapping as compared to e-commerce or streaming services.
A common theme for all methods is that serious consideration must be taken when choosing the condition to trigger them in order to create a timely, relevant and non-obtrusive experience for your users. For example, you can use a risk based approach to trigger email alerts on suspicious logins, or transactions, rather than asking the user for verification every time.
If you don't have time to read the whole article, here is an overview table.
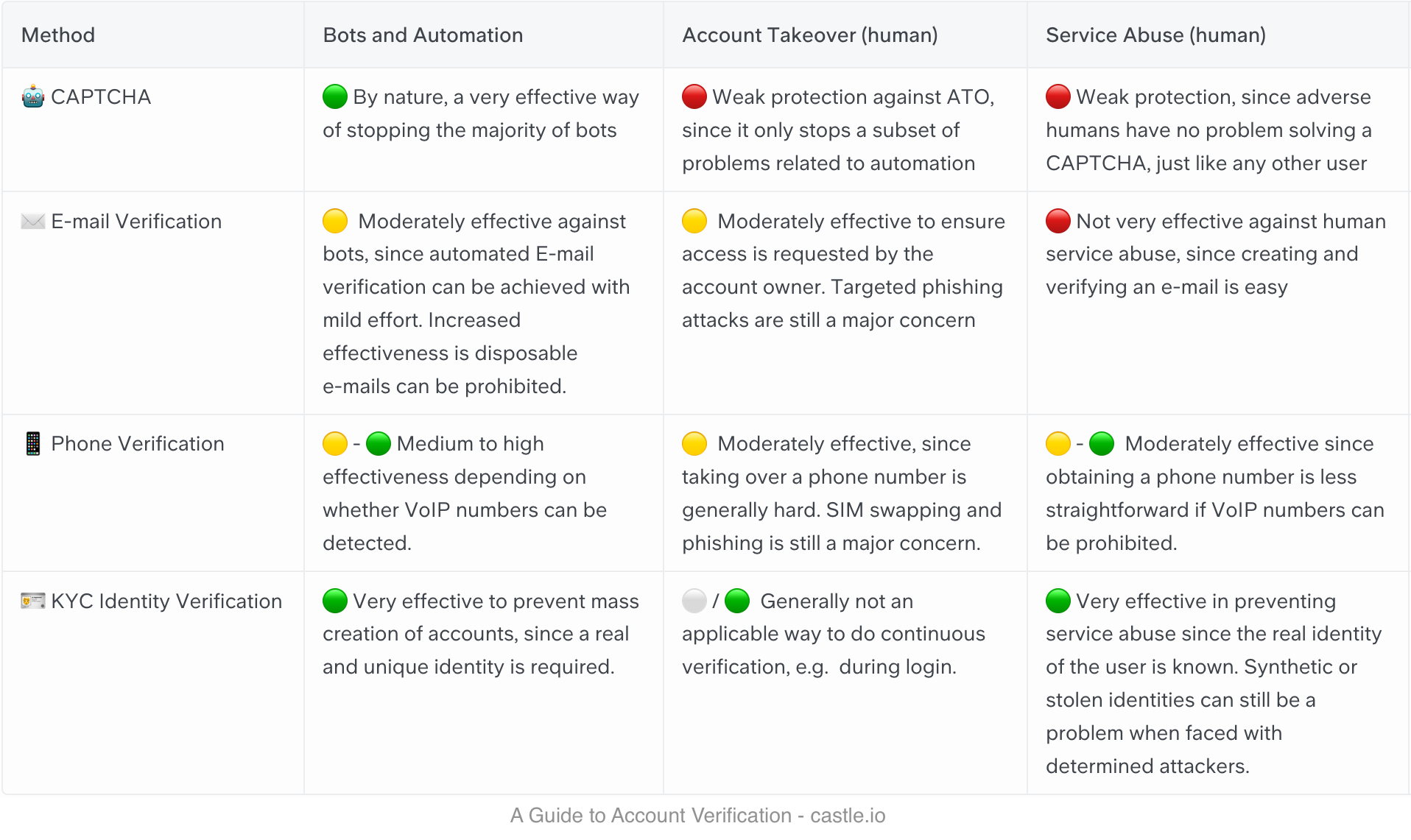
Defining a objective level of protection is not straighforward, but the three-color rating system I’m using is defined as follows:
- 🟢 Good protection means that it requires significant effort and/or money to get around the verification with malicious intent, and without exposing your identity.
- 🟡 Moderate protection means that it requires some effort, like scripting/coding or acquiring a new e-mail address or phone number
- 🔴 Weak protection means that it’s easy for a person to get around the verification with minimal cost and effort.
Now let's dive in and compare the different verification methods.
CAPTCHA
CAPTCHAs are ubiquitous on the internet. They are designed to filter out bot traffic by presenting a small puzzle or problem that requires little or no effort for a human to solve but is hard for a script/computer. CAPTCHAs require minimal implementation effort since users can complete the puzzle directly in the browser. A wide range of options is available, from open source versions like Slider Captcha to free options like Google reCAPTCHA, hCAPTCHA, and commercial solutions such as Arkose Labs.
Effectiveness:
- 🟢 Bots and automation: CAPTCHAs are generally very effective at stopping most bots, as they aim to separate bots from humans. Solving them programmatically requires high effort, or attackers have to resort to paying for a CAPTCHA farm to bypass it at scale.
- 🔴 Account takeover: CAPTCHAs are generally not very effective against account takeovers since they don't ensure anything related to the user's identity. However, they can help prevent brute force or credential stuffing attacks.
- 🔴 Service abuse: Similar to account takeover, CAPTCHAs are not very effective at stopping service abuse unless automated. Humans can easily solve CAPTCHAs and continue with nefarious activities.
Drawbacks:
- Negative user experience may lead to lower conversion, especially if triggered too often for legitimate users.
- May hinder accessibility for some users.
- No insight into the number or type of users challenged unless this is explicitly tracked.
- Doesn't stop the most sophisticated bots.
Email verification
Email verification is a standard practice, often used at the account registration phase to confirm that the user entered the correct email address. However, it can also be used to confirm the account owner once again when performing sensitive operations, such as transactions. The typical implementation consists of an email message containing either a link for the user to click or a one-time code to enter in the application form.
Effectiveness:
- 🟡 Bots and automation: E-mail verification is moderately effective against bots, since the verification process, which is typically clicking a link in the e-mail, requires some additional effort to implement as part of automation.
- 🟡 Account takeover: If a suspicious login is detected, email verification is generally effective at ensuring that access is requested by the legitimate user. However, to guard against phishing attacks and cases where the user's email account has been compromised, an additional verification factor, such as phone or OTP code, is recommended for better protection.
- 🔴 Service abuse: Similar to CAPTCHA, email verification is not very effective against service abuse, unless this is carried out by automation, since acquiring and verifying a new email address is easy for a determined, human attacker.
Drawbacks:
- Not foolproof, disposable emails can be used by sophisticated bots to complete the verification. You can choose to deny disposable emails, but this comes at the expense of potentially shutting out privacy minded users.
- Time-consuming for users. If triggered too often, this can become annoying for users, and cause lower conversion.
- Won’t deter determined attackers, since obtaining an email address is easy.
- Less effective against Account Takeover if the legitimate user has lost access to their email.
Phone verification
Verifying an account via phone number is similar to email verification, as the user needs to tap on a link or enter a one-time code. The difference is that a phone number is generally harder to obtain than an email address, and it is a stronger tie to the user's identity.
Effectiveness:
- 🟡- 🟢 Bots and automation: Phone verification provides moderate protection against bots, since similar to email, scripted access to create and retrieve text messages can be achieved with some effort. However, if VoIP type numbers can be accurately detected and blocked, phone number verification can be quite effective against bots.
- 🟡 Account takeover: Similar to email verification, phone verification provides decent protection against account takeover. However, users are still susceptible to phishing and SIM swapping attacks, where the attacker gains control over the phone number. The risk for this is particularly high where there is high value associated with each account, such as banking or crypto.
- 🟡- 🟢 Service abuse: Similar to mitigating bots, phone verification is a moderately effective way of preventing service abuse, but is quite effective if combined with prohibiting VoIP numbers, since this makes acquiring multiple phone numbers way harder.
Drawbacks:
- Pricey, as there is a significant cost associated with each check. Other than annoying users, if SMS is used in a flow that could be triggered by bots, the bill can escalate quickly.
- Have to be paired with phone lookup services, like Twilio or Telesign, in order to detect and prevent automated VoIP numbers.
- Intrusive and may raise privacy concerns.
- Time-consuming for users
- May exclude users without access to a phone number (or the ones that are not willing to give it up)
KYC Identity verification
KYC Identity verification is the process of collecting and verifying documents or other proof of a user's real identity. This type of verification is mostly applicable in fintech services at the registration phase, where there typically are KYC (Know Your Customer) regulations in place, but is included in this guide for completeness.
Effectiveness:
- 🟢 Bots and automation: Very effective against bots and automation since the verification process is heavy and usually requires physical documents and a live photo.
- ⚪ / 🟢 Account takeover: Generally not applicable for account takeover since this level of security is too costly and intrusive to deploy at login. It can be used as a reliable way of recovering access to a stolen, locked account, but would then require the identity to be associated with the account at registration.
- 🟢 Service Abuse. Provides very good protection against service abuse since the real identity of the individual is known, creating accountability. However, it is not bulletproof, as stolen identities can be used by determined attackers.
Drawbacks:
- Pricey, as there is a significant cost associated with each check.
- Intrusive, requires a lot of effort from the user, and providing this much personal information is typically only acceptable in fintech services where KYC is a requirement.
- Limited practical use: Typically only applicable at registration and not as a continuous verification method, e.g., to verify a suspicious login.
As you can see, stopping human service abuse is generally a very hard problem to solve without requiring a lot of personal data to verify the person's identity. This is fine if you run a fintech service and need to have very strict KYC processes, but more problematic if you run a content platform, as it may create too much friction for users and create roadblocks to quick and easy conversions.
There is no one-size-fits-all solution when it comes to account verification methods. Each method has its own strengths and weaknesses, and the effectiveness of each depends on the specific type of fraud or abuse you're trying to prevent. It's crucial to carefully consider the unique needs of your service and strike the right balance between security, privacy, and user experience.
When implementing account verification methods, remember to:
- Evaluate the type of fraud or abuse you're trying to prevent and choose the appropriate method accordingly.
- Be mindful of the user experience, ensuring that verification methods are not overly intrusive or time-consuming.
- Monitor the performance of your chosen methods and be prepared to adjust as necessary to maintain the right balance between security and growth.
By taking a thoughtful approach to account verification, you can significantly reduce fraud and abuse on your platform while maintaining a positive user experience and fostering trust among your users.
With this in mind, Castle provides an API that allows you to take a risk based approach to invoking account verification, allowing you to create a better user experience while at the same time saving money on costly methods like SMS or KYC checks Feel free to reach out to learn more or schedule a demo on how Castle can help!



